Cybersecurity has become more critical with the increased frequency and sophistication of cyber-attacks. But finding a practical and simple solution is not easy, and there are many things to consider, from getting buy-in and support from upper management to finding credible and experienced resources to manage the security elements in your environment.
Here you will find:
Challenges Organizations Face with Security
ProServeIT's Cybersecurity House Model
Simplifying Security Using a Three-Step Approach
ProServeIT Academy: Cybersecurity Course
Businesses need to implement effective cybersecurity measures to protect themselves from cyberattack risks.This blog will demystify the complex cybersecurity landscape, guiding you through our Cybersecurity House Model and a pragmatic three-step approach.
Challenges Organizations Face with Security
Many organizations are attempting to safeguard their expanding digital domain from ever-increasing cyber threats. During COVID times, many companies pushed the limits of their estate beyond the physical network boundary. Some might be in a hybrid situation where servers remain on-premises, while other services are in the cloud. Others might simply utilize their mobile devices to access corporate data stored in the cloud. Some users may utilize their own devices to connect to corporate resources but are uncertain how safe those personal devices are.
Common Cybersecurity Challenges
It is becoming increasingly challenging to protect organizations’ information and assets, and here are some of the reasons:
☑️ Attack techniques, frequency and complexity are evolving extremely fast.
☑️ Security teams are under strain from the expanding range of defensive technologies and not knowing what security tools they need as hybrid cloud adoption increases.
☑️ The need for skilled security professionals has dramatically increased, but supply cannot meet current or future demand.
☑️ High volume of noisy alerts causes alert fatigue
☑️ Too many disconnected products and lack of automation

ProServeIT's Cybersecurity House Model
ProServeIT’s Cybersecurity House model is a comprehensive guide, akin to a blueprint, for constructing your cybersecurity framework. Think of it as a real house, with a foundation, pillars, ceiling, and roof. This intuitive structure simplifies the complex field of cybersecurity, helping you understand the essential elements needed.
You can easily understand the elements you need to build your cybersecurity framework with this model. 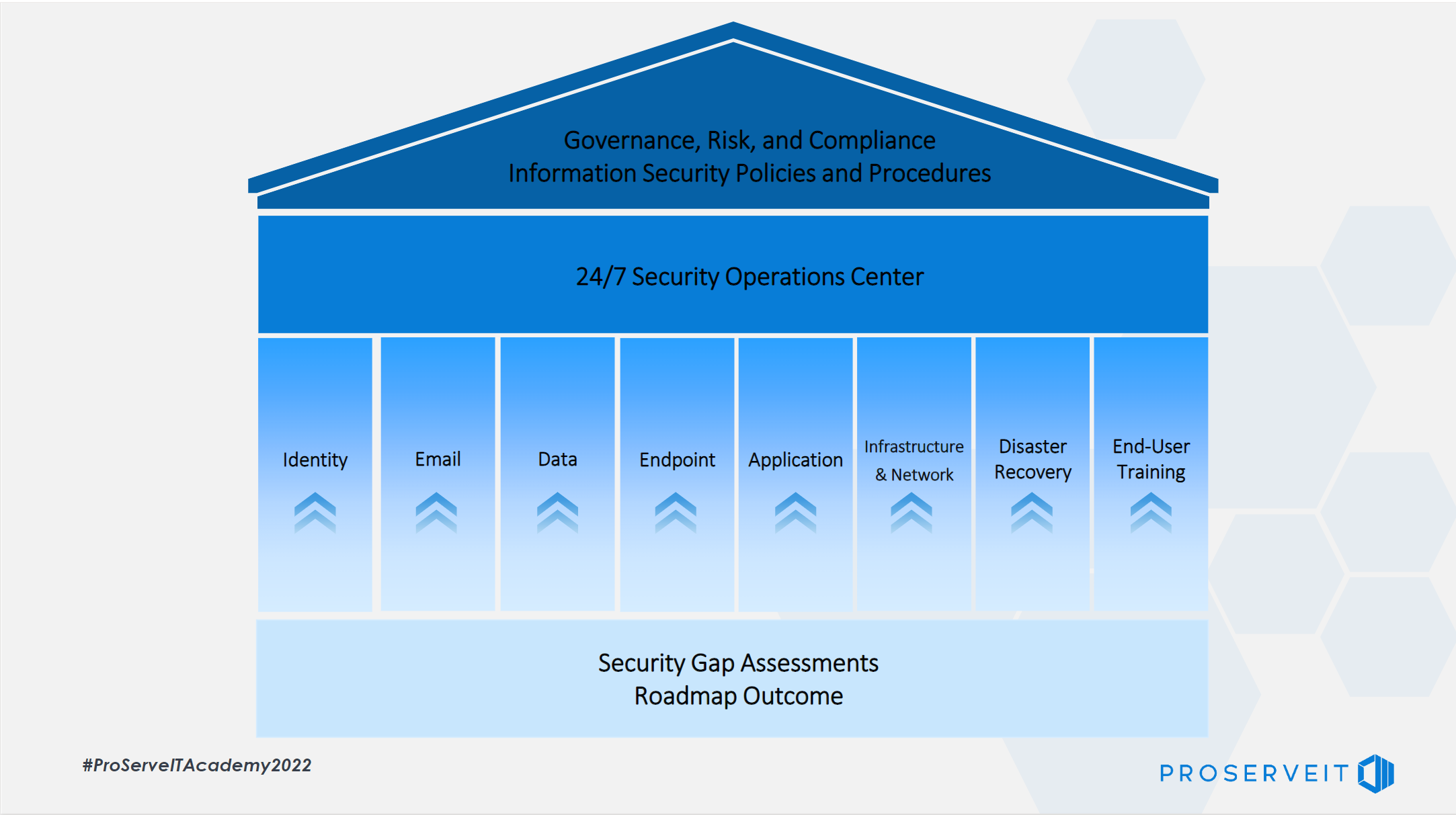
Foundation
Every house needs a solid foundation to build on, otherwise it would fall. In the Cybersecurity House Model, the foundation includes:
☑️ Security assessments with an outcome being a road map.
☑️ Vision of the desired state of your organization.
☑️ Mission and purpose of an assessment.
☑️ Strategy, a long-term plan of your actions and priorities.
When the foundation is clear and communicated to all stakeholders, it will help everyone to make decisions quickly and eventually implement the following pillars.
Pillar
The Pillars support the ceiling and the roof of the house. Without these supporting pillars, the ceiling and roof would fall. In our Cybersecurity House model, these pillars are the protection mechanisms we put in place. Each of those pillars represents what organizations should consider or should have to be more secure and have a secure baseline.
Once the assessment is complete, each pillar will be categorized by a level based on what the organization has. The road map will be associated with your organization's desired security state for each pillar, which depends on how much you want to invest, your resources, upper management support and buy-in, and other factors.
Ceiling and Roof
The Ceiling holds all the pillars together, and the pillars support the ceiling as well. To put your organization in a secure state, you need to monitor your identities, emails, data, and endpoints (devices and network access) for any security risks. Therefore, you need an active monitoring solution or a security operations center that can continuously monitor your environment for threats. This is where Security Information and Event Management (SIEM) and Security Orchestration, Automation and Response (SOAR) applications come into play.
The Roof shields the house from things that can hurt it, so ProServeIT's Cybersecurity House model is where our information security policies come into play to govern all the policies and procedures. It also regulates information protection and sets rules and procedures for all individuals accessing and using your organization's IT assets and resources. The roof also oversees the cybersecurity teams responsible for mitigating business risks.
Simplifying Security Using a Three-step Approach
With ProserveIt’s three-step approach, you can simplify your security solutions. The first phase, Assess, is the foundation of the House to identify gaps and areas of improvement and create a security roadmap. The second phase, Protect, is the pillars part of the House model where you can deploy various Microsoft security technologies to close the gaps identified in the assessment phase. The last phase, Monitor and Improve, is the ceiling and roof to monitor the service to ensure compliance and report malicious activities. This three-step approach should be looped until your organization is fully secure.
Step 1. Security Assessment
Kinds of Cybersecurity Assessments
Organizations can complete various assessments according to their needs, including:
☑️ Microsoft Office 365 Security Assessment
☑️ Microsoft Azure Security Assessment
☑️ Microsoft Domain Security Assessment
☑️ Microsoft Threat Check Security Assessment
☑️ Rapid Cyberattack Security Assessment
☑️ Microsoft Secure Score Security Assessment
☑️ Phishing Campaign Assessment
☑️ Penetration Testing Assessment
☑️ Vulnerability Assessment
The more information you have about the risks to your organization, the better you can identify what needs to be in your implementation plan to mitigate those risks. That's the main reason for performing these types of assessments.
ProServeIT's Three-Phased Cybersecurity Assessment
ProServeIT performs cybersecurity assessments in a three-phased approach to help you understand your organization’s security level and improve from your current level to your desired state.
🗒️ Holistic Questionnaire: To understand the desired state from a security perspective and how a company approaches security topics.
🔎 Security Maturity Exercise: To understand where the organization fits between Level 0 to Level 3 and rate each level of security or each component within the security model on whether you’re going to be reactive, proactive or optimized.
☑️ Level 0. Unprepared: Organizations lack the necessary information to take effective action. Unaware or unable to respond to current or emerging threats.
☑️ Level 1. Reactive: Organizations have basic platforms and structures to react to business requirements. Cannot proactively prevent threats from arising.
☑️ Level 2. Proactive: Organizations have platforms, structures, and organizational processes to address current issues and challenges proactively.
☑️ Level 3. Optimized: Organizations have platforms, structures, and organizational processes to address future issues and challenges proactively.
🎯 Audit of Environment: To provide the company with the best results and recommendations to make an informed decision on what needs to be done next.

Step 2. Protect
Organizations would have to tag all risks uncovered in the assessment document to mitigate the risk to a level they want to target with solutions such as:
🧑🤝🧑 Identity: Azure Active Directory, Multi-Factor Authentication, Conditional Access Policies, Self Service Password Reset, Azure Privileged Identity Management, Azure Active Directory Single Sign On, Azure Active Directory Identity Protection, Microsoft Defender for Identity.
✉️ Email: Phishing Campaigns, Microsoft Defender for Office 365, Exchange Online Protection, Spoof Protection (SPF, DKIM, DMARC), Office 365 Message Encryption, Data Loss Prevention, Retention Policies.
🔥 Disaster Recovery: Microsoft Azure Backup, Microsoft Azure Site Recovery, Microsoft Azure Archive Storage, Document BCDR Plan, Recovery Time Objective (RTO), Recovery Point Objective (RPO).
📊 Data: Microsoft Information Protection, Data Loss Prevention, Retention Policies, Microsoft Defender for Endpoints, Microsoft Azure Backup, Microsoft Azure Site Recovery.
🌐 Infrastructure & Network: Network segmentation\Isolation, Security Information and Event Management (SIEM), Security Orchestration Automation and Response (SOAR), Just-in-Time Access.
🛡️ Governance, Risk & Compliance: Microsoft Purview, Data Loss Prevention, Microsoft Information Protection, Microsoft Azure Blueprints.
🖥️ Endpoints/Devices: Microsoft Intune, Microsoft Autopilot, Microsoft Defender for Endpoints.
☁️ Applications: Microsoft Cloud App Security, Shadow IT, Azure Active Directory Single Sign On, Conditional Access Policies.
📚 Training: End User Awareness Training, Phishing Campaigns, Executive\Leadership Security Training.
Organizations should follow the recommended plan and act on it when they find a gap. Depending on the risks involved and how much risk the organization is willing to tolerate, and where they fall on the maturity level, there may be solutions that fit their needs to reduce risk as much as possible.
.png?width=960&height=618&name=Workplace-copillot-productivity%20(1).png)
Step 3. Monitor and Improve
The third step is to monitor and improve. The best solution for this stage would be Security Information and Event Management (SIEM) applications like Microsoft Sentinel.
Microsoft Sentinel: End-to-end solution for security operations
Microsoft Sentinel is a scalable and cloud-native SIEM (Security Information and Event Management) and SOAR (Security, Orchestration, Automation and Response) solution. We want to detect targeted attacks and data breaches as soon as possible, so we'll be able to analyze event information in real-time. SIEM also enables us to collect, store, and investigate log data for incident response, forensics, and regulatory compliance. A playbook creation tool helps security teams move from gathering data to streamlined security operations, automating numerous procedures to respond to security incidents.
📑Phase 1. Collect: Microsoft Sentinel offers a simple ingestion process through data connectors such as a Cisco Firewall or Palo Alto Firewalls, which makes it easy to get started with Microsoft or third-party security solutions. Currently, there are 123 different connectors available for Microsoft Sentinel, and the list is growing.
📝 Phase 2. Detect: After collecting all the logs, Microsoft Sentinel creates analytic rules to alert on possible security incidents. Various rule types are available, some of which are guided by artificial intelligence (AI).
🔎 Phase 3. Investigate: The third phase of Microsoft Sentinel, investigate, helps you understand the scope of the incident and find the root cause of a potential security threat.
⚙️ Phase 4. Respond: The last phase, response, allows you to automate workflows by creating "playbooks" using logic apps, which makes it easy to take action and resolve incidents quickly.
Have you also read?
New Microsoft Cybersecurity Solutions | Tech News: August 2022
How to Protect your Corporate Web Applications from Cyber Attacks
How to Improve Your Organization’s Cybersecurity: A Beginners Guide
Alarm Guardian: Managed Services Packages
ProServeIT’s Alarm Guardian is similar to installing an alarm system at your home: you can get all the parts required to safeguard your house - cameras, sensors, locks, and so on - and install and monitor them yourself. Isn't it better to have professionals handle everything for you? ProServeIT helps you monitor and improve your organization’s security posture while preventing, detecting, analyzing, and responding to cybersecurity incidents around the clock.
ProServeIT's Alarm Guardian not only installs your new security system but also provides proactive security monitoring and upgrades to keep your digital assets safe. With Microsoft Sentinel as the monitoring station, ProServeIT's Alarm Guardian is constantly looking for potential threats, so you don't have to.
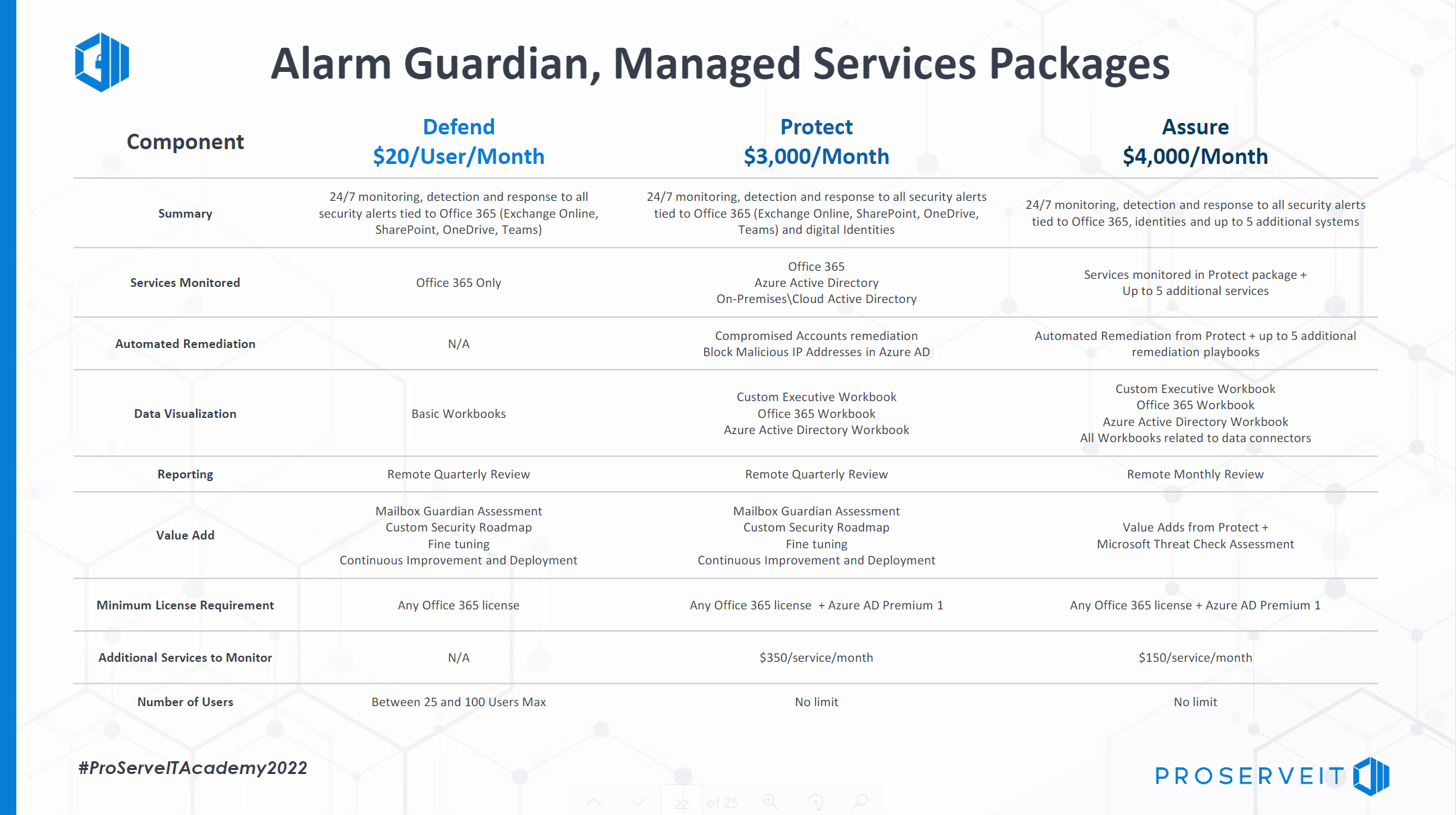 Alarm Guardian is available in three tiers, each offering different levels of protection. Tier 1 is ideal for organizations with less than 100 users, while Tier 2 is designed for organizations that want ProServeIT to monitor more than just their Office 365 environment. Tier 3 offers the most comprehensive monitoring and assurance package for organizations that want the highest level of protection.
Alarm Guardian is available in three tiers, each offering different levels of protection. Tier 1 is ideal for organizations with less than 100 users, while Tier 2 is designed for organizations that want ProServeIT to monitor more than just their Office 365 environment. Tier 3 offers the most comprehensive monitoring and assurance package for organizations that want the highest level of protection.
Alarm Guardian is a powerful security solution that can help your organization protect itself from potential cyber threats. ProServeIT will help you find which package is right for your organization. Contact us to learn more!
ProServeIT Academy: Cybersecurity Course
Every home needs a solid foundation before you construct the main floor. What it means to have security as the basis of your Technology Strategy Framework is that you want to ensure that future technologies are protected by design and don't pose any new risks for your company.
George Abou-Samra, Principal Consultant and Security Practice Lead, and ProServeIT Academy's Cybersecurity Course will give you all the information you need to protect your organization. Learn more about the ProServeIT Academy Cybersecurity Course for IT professionals and IT leaders here.
Tags:
January 11, 2024

Comments