The ability to detect threats and glean relevant data from possible threat patterns is important for organizations when it comes to their cybersecurity protocols. Being prepared for a cyberattack is becoming a more prevalent issue around the world. According to research by Cybersecurity Ventures, global cybercrime costs are expected to grow by 15% per year over the next five years, reaching $10.5 trillion annually by 2025.
Microsoft is dedicated to developing better security products to help give peace of mind to its thousands of customers globally. This way, organizations can focus on improving their daily operations and business goals while having confidence in the strength of their current cybersecurity.
In this blog post, we will discuss how Microsoft’s new threat intelligence solutions can help with tracking any threats and improving your current cybersecurity posture.
In this blog you will find:
Microsoft’s focus on improved cybersecurity
Use Microsoft Defender Threat Intelligence to track threat actor activity & patterns
Use Microsoft Defender External Attack Surface Management to uncover your cyber vulnerabilities
Conclusion
With the uncertainty linked to organizational cyber risk, it is important for companies to stay up to date on the best cybersecurity solutions and protocols. By showcasing its cybersecurity efforts, a company can help reassure its existing customer base that their data is secured using the best technology possible.
It is especially important to be transparent about your organization’s cybersecurity effort. According to a study by Arcserve, 70% of consumers believe businesses aren't doing enough to secure their personal information. To further highlight what the impact of quality cybersecurity means for a business, the same study emphasized that 25% of consumers will abandon a product or service in favor of a competitor after a single ransomware-related service incident.
Microsoft’s focus on improved cybersecurity
By constantly accumulating signal and threat intelligence across the digital environment, Microsoft is well equipped to track threat actors much more closely and better identify their behavior over time. The immense volume of intelligence obtained from its products and platform gives Microsoft exceptional insights to help thoroughly protect its customers both internally and externally.
Here are some key points to note:
- - As of today, Microsoft tracks 35 ransomware families, and more than 250 unique nation-states, cybercriminals, and other threat actors.
- - Microsoft’s cloud processes and analyzes more than 43 trillion security signals every single day.
With its acquisition of RiskIQ (a leader in global threat intelligence and attack surface management) in 2021, Microsoft is better positioned to develop world-class threat intelligence, monitor any susceptible internet-facing assets and to help develop a more comprehensive view of the global threats to its customers’ businesses.
Guided by its vision to provide unmatched, actionable threat intelligence, Microsoft is pleased to announce two new security products that provide richer context into threat actor activity and help organizations lock down their infrastructure and reduce their overall attack surface.
Take a look below for more details on these new security products.
Use Microsoft Defender Threat Intelligence to track threat actor activity & patterns
Microsoft Defender Threat Intelligence is a complete cloud-based threat intelligence platform which enables IT security professionals to analyze and act upon signals collected by a global collection network and processed by security experts and machine learning. The amount, scale, and depth of intelligence is constructed to enable security operations centers (SOCs) to recognize the threats specific to their organization and to reinforce their security posture appropriately.
Utilizing Microsoft Defender Threat Intelligence can help your organization to do the following:
- ⚙️Accelerate detection and remediation: Discover the full scope of an attack. Understand an online adversary’s entire toolkit, prevent access by all their machines and known entities, and continuously block a single IP address or domain.
- 🔒Enhance your security tools and workflows: Extend the reach and visibility of your existing security investments. Use raw cyberthreat intelligence from effective security tools to gain more context and understand threats more deeply.
- 🔍Identify attackers and their tools: Understand how your online connections work and identify your potential threat exposures with a complete cyber threat map of the internet.
Microsoft Defender Threat Intelligence helps to safeguard organizations from modern adversaries and threats like ransomware. Unlike its other security products such as Microsoft Sentinel and the Microsoft Defender family, this new solution offers immediate access to real-time data from Microsoft’s unparalleled security signals. The diagram below shows how this solution works.

The data sets obtained from this solution reveal the infrastructure connections across the global threat landscape, unveiling an organization’s external attack surface and empowering teams to investigate the tools and systems used to attack it. Defender Threat Intelligence provides external context for internal security incidents via SIEM (security information and event management) and XDR (extended detection and response) capabilities in Microsoft Sentinel and Microsoft 365 Defender.
Use Microsoft Defender External Attack Surface Management to uncover your cyber vulnerabilities
As many businesses adapt to the current economic climate, they might own a number of internet-facing assets that may have been overlooked in cyber security planning.
Such assets can be created by:
- Mergers and acquisitions
- Exposure from business partners
- Shadow IT (technology used without explicit IT department approval or knowledge)
- Sudden business growth
- Incomplete cataloging
Microsoft Defender External Attack Surface Management can help companies to view themselves from the perspective of an attacker so that any key gaps can be unveiled and properly addressed to reduce the risk of future attacks. This new solution scans the internet and its connections daily. Doing this helps create a complete catalog of a customer’s environment, discovering internet-facing resources (including agentless and unmanaged assets).
Utilizing Microsoft Defender External Attack Surface Management can help your organization to do the following:
- Attain Multicloud visibility: Maintain a dynamic inventory of external resources across multiple cloud and hybrid environments.
- Identify exposed weaknesses: Prioritize vulnerabilities and misconfigurations hidden in unmanaged resources, allowing you to bring the resources under management to remove those exposures
- Discover unmanaged resources: Understand the full extent of your attack surface, including shadow IT and assets created through common, everyday business growth.
To better safeguard its digital presence across the cloud and the internet, an organization can improve the defense of its internal network and much more by using Microsoft Defender External Attack Surface Management. See the diagram below for a good example of this.
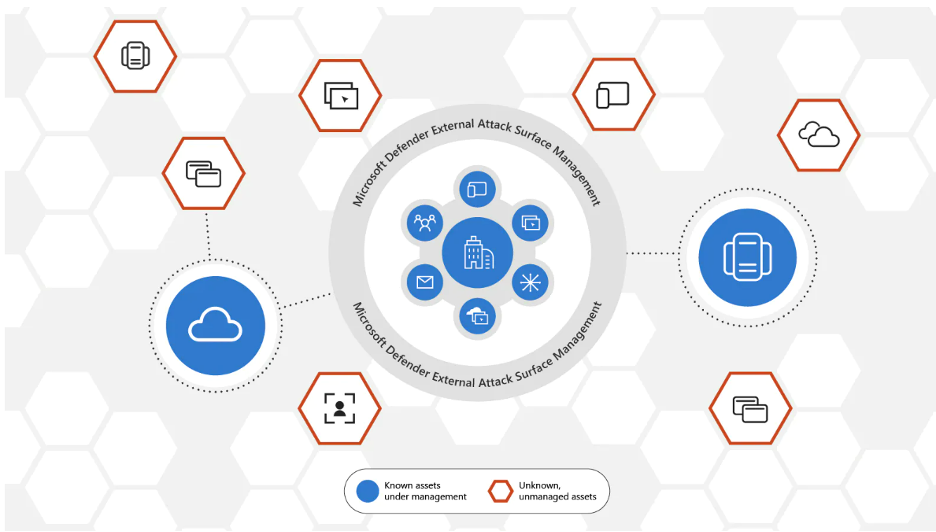
Because this Microsoft solution maps an organization’s internet-exposed presence, it helps provide complete visibility into managed and unmanaged external resources to understand the attack surface and classify and prioritize vulnerabilities, misconfigurations, and exposures.
Outfitted with the visibility granted by Microsoft Defender External Attack Surface Management, organizations can improve their security posture and become more resilient to attacks. This can help with risk mitigation by using Microsoft’s SIEM and XDR tools to help bring an organization’s endpoints, unknown resources and assets under secure management.
Conclusion
Microsoft is laser-focused on improving cybersecurity for all its customers. One way it’s doing this is by providing powerful tools like Defender Threat Intelligence and External Attack Surface Management. These tools allow you to track threat actor activity and patterns, as well as uncover your cyber vulnerabilities.
With this knowledge, you can take steps to improve your organization's current cybersecurity posture and protect your valuable data. Interested in improving your organization's current cybersecurity? Discover how ProServeIT can help by clicking this link today.
Tags:

August 11, 2022
Comments