Welcome to the Cybersecurity Course
Safeguard your organization with cutting-edge cybersecurity strategies designed to tackle the most pressing security challenges. This Cybersecurity course covers identity, email, and data security foundations and includes live demonstrations of real-world attacks and defenses.
Registration includes access to all upcoming and previous webinars, ensuring a well-rounded understanding of cybersecurity foundations.
Upcoming webinars in this course:
- Topics will be announced soon!
These cybersecurity online webinars are tailored for IT leaders and professionals looking to strengthen their security posture and protect their corporate environments from evolving threats.
Register for Upcoming & On-Demand Webinars
Security Foundations: Identity Protection
This webinar explores:
• Advanced identity security strategies to protect your Microsoft environment.
• How AI can impact and strengthen your security approach.
• Live demo: Applying Conditional Access policies after a password compromise and restricting access to corporate devices.
• Live demo: MFA bypass attack and key defenses.
Security Foundations: Email Protection
This webinar explores:
• The evolving threats in email security and how to defend against them.
• The impact of AI on email security.
• Live demo: How attackers can create phishing pages, compromise user credentials, and extract valuable information.
• Tools and tactics to stay ahead of email-based attacks.
Security Foundations: Data Protection
This webinar explores:
• Cutting-edge data security measures to protect sensitive information.
• How AI can impact your data protection strategy.
• Live demo: Preventing sensitive information from being shared externally using Microsoft’s Data Loss Prevention (DLP) capabilities.
• Best practices for strengthening your data security posture and ensuring compliance.

About the Instructor
George Abou-Samra
Principal Consultant and Security Practice Lead, ProServeIT
George Abou-Samra is a Principal Consultant and Security Practice Lead at ProServeIT. As Security Consultant, George's primary focus revolves around ensuring that ProServeIT's customers and organizations in general are made aware of the increase in cybersecurity risks, as well as providing guidance on what to do to better secure their organizations from threats and bad actors. George's extensive technical background is supplemented by his expertise in white-hat hacking, gaining a better understanding of the methods that hackers would employ to break into a customer's environment, and utilizing that knowledge to better protect the customers he works with on securing vulnerable points of entry. When George isn't working, he enjoys spending time with his family, playing basketball, and hiking through the beautiful trails in Ontario and Canada.
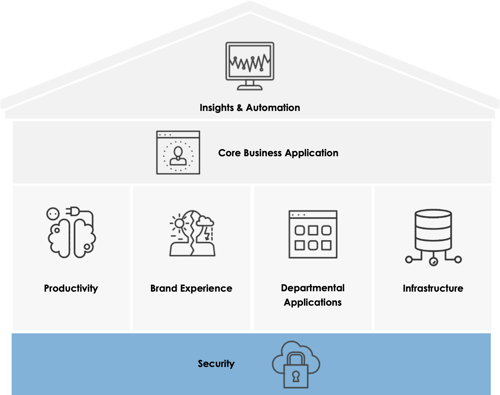
Where does the Cybersecurity course fit within your technology strategy?
Every house needs a solid foundation before the main floor is built.
What it means to have security as the foundation of your Technology Strategy Framework is, as you’re making technology investment decisions, you want to make sure that the new technologies are secured by design and that they’re not going to introduce any additional risks to your business.
Join George to understand better on how you can create that strong foundation for your Technology House.
To learn more about each room of The House, have a look at our blog, The CEO’s Technology Strategy Framework.
Other ProServeIT Academy Courses
Simplifying Your Security Journey
Microsoft's Zero Trust Model
Ransomware as a Service: How to Protect Your Organization
Protect Against Phishing Scams and Identity Theft
The Good and Bad of AI in Cybersecurity
Improve Your Insurability and Protect Your Business
Secure Your Workforce with Microsoft Intune
Defend smarter with Alarm Guardian MXDR