What Is IT Security & Why It Matters More Than Ever
As our reliance on digital technology deepens, the importance of cybersecurity continues to grow exponentially. According to a Morgan Stanley article, AI has facilitated the development of advanced threats like deepfakes and sophisticated phishing attacks, which are increasingly difficult to detect and defend against. At the same time, AI is also becoming an indispensable tool for cybersecurity professionals, offering advanced detection mechanisms, predictive analytics, and automated responses to potential threats. This "double-edged sword" nature of AI underscores the necessity for continuous advancements in cybersecurity tactics and technologies.
In this blog, you will find:
🛡️ What is Artificial Intelligence(AI) for Cybersecurity?
⛔ The Rise of AI-Powered Cyberattacks
⚔️ AI-Driven Security Tools for Defense: Fortifying the Cybersecurity Barrier
💡 What is Microsoft's Perspective on AI Security?
⏰ Protect Your Business with ProServeIT's AI-driven Alarm Guardian
🏛️ ROM Enhanced Cybersecurity with Alarm Guardian
This blog explores AI's role in cybersecurity, including its applications in combating threats and enhancing protection. It highlights Microsoft's use of AI for cybersecurity and discusses ProServeIT's Alarm Guardian for threat detection. Discover how to effectively harness AI's power to bolster security measures.
What is Artificial Intelligence (AI) for Cybersecurity?
Artificial Intelligence for cybersecurity scrutinizes and correlates event and threat data from various sources, transforming it into clear, actionable insights for security professionals to investigate, respond to, and report on. If a cyberattack meets the security team's predefined criteria, AI can automate the response and isolate affected assets.

The Rise of AI-Powered Cyberattacks
According to a 2023 Global CISO Survey by Heidrick & Struggles, 46% of CISOs identified AI and machine learning as the most significant cyber risks. AI advancements can also lead to false positives in identifying cyber threats, where legitimate actions are mistakenly flagged as malicious. This dark side of Artificial Intelligence’s rapid advancements has empowered cybercriminals to develop more sophisticated and large-scale attacks. Here are some scenarios illustrating how AI can be used in cyberattacks.

Automated Tasks and Attacks Launched at Scale
AI can automate repetitive tasks much faster than humans, allowing cybercriminals to easily launch large-scale attacks. This includes brute force attacks, where AI systems can rapidly input numerous password combinations to breach accounts, or automated scraping of public databases for personal information that can be used in other criminal activities.
AI can disrupt traditional security operations by automating rapid large-scale attacks, making it crucial for security teams to enhance their operational effectiveness and identify threats in real time.
AI-Generated Phishing and Social Engineering
Cybercriminals can utilize AI to craft highly personalized phishing emails that are more difficult to distinguish from legitimate communications, a technique known as social engineering. AI algorithms can analyze user behavior, examining patterns and anomalies in a victim’s online actions, to create tailored messages that appear credible. Deepfake technology, which uses AI to create realistic audio and video impersonations, can also manipulate individuals into divulging sensitive information or transferring funds to fraudulent accounts.
Vulnerability Identification and Exploitation
AI can analyze data to identify vulnerabilities within software and systems much quicker than traditional methods. Once these vulnerabilities are found, they can be exploited before they are patched. AI systems can also adapt to different environments, learning to navigate complex systems to find exploitable flaws.
AI-Driven Security for Defense: Fortifying the Cybersecurity Barrier
With cyberattacks' ever-evolving sophistication, traditional security methods are no longer enough to keep sensitive data and systems safe. That’s where AI-powered cybersecurity tools come into play, offering enhanced protection against advanced threats. AI assists security professionals by simplifying reporting, enhancing endpoint security and management, providing cyber threat analysis and insights, and improving incident investigation and response. Below are three examples of AI-driven security scenarios that are becoming essential in contemporary cybersecurity operations.
Analyzing Vast Amounts of Data to Identify Threats and Anomalies in Real Time
Artificial intelligence has revolutionized cybersecurity by enhancing our ability to analyze large datasets and uncover patterns indicative of potential threats. Advanced machine learning algorithms can sift through vast network traffic, identifying anomalies that would be nearly impossible for human analysts to detect in real-time. By recognizing unusual behavior promptly, AI systems can flag potential security breaches, enabling organizations to act preemptively. This real-time analysis is crucial for mitigating the impact of cyberattacks and maintaining robust security postures. Additionally, AI helps security analysts by processing massive amounts of data, providing rapid insights, and cutting through the noise of daily security alerts and false positives, drastically improving team efficiency and productivity.
Automating Threat Detection and Response
One of the most significant advantages of AI in cybersecurity is its ability to automate threat detection and incident response. Traditional methods of identifying and addressing cyber threats are time-consuming and labor-intensive. AI-driven systems can rapidly detect anomalies and potential threats, triggering automated responses to neutralize the risks. This enhances the capabilities of the security team by allowing them to automate threat detection and response, isolate affected assets, and leverage AI for incident investigation and response. This accelerates the response time and reduces the burden on cybersecurity professionals, allowing them to focus on more complex tasks. Faster intervention means reduced damage and securing critical assets before significant harm can occur.
Strengthening Password Security and Access Controls
AI is also instrumental in fortifying password security and enhancing access control measures. By analyzing user behaviors and identifying patterns, AI helps security teams manage access controls and detect suspicious login attempts. Additionally, AI-driven solutions can recommend stronger, context-aware passwords and monitor for potential breaches in real time. These systems can employ multi-factor authentication, adaptive authentication methods, and other sophisticated access control mechanisms to ensure that only authorized users gain entry to sensitive systems. According to a report by IBM, incorporating AI into access control significantly reduces the risk of unauthorized access and data breaches.
What is Microsoft's Perspective on AI Security?
Recognizing AI's dual capabilities in launching and safeguarding against cyber threats, Microsoft consistently invests in AI-driven security solutions to proactively tackle the ever-changing landscape of cybersecurity challenges. With a holistic approach, Microsoft has developed an intricate ecosystem that strategically incorporates AI-powered solutions to bolster cybersecurity measures.
One notable example is Microsoft Defender for Endpoint, which leverages AI to outmaneuver sophisticated adversaries, stopping cyberattacks like ransomware at machine speed. It boosts prevention with global threat intelligence, clearly showing your cyberattack surface and adversaries and providing best practices for cyber threat prevention. Additionally, it ensures end-to-end security for your multiplatform and Internet of Things (IoT) devices with a comprehensive, next-generation antivirus, detection, and response solution at its core.
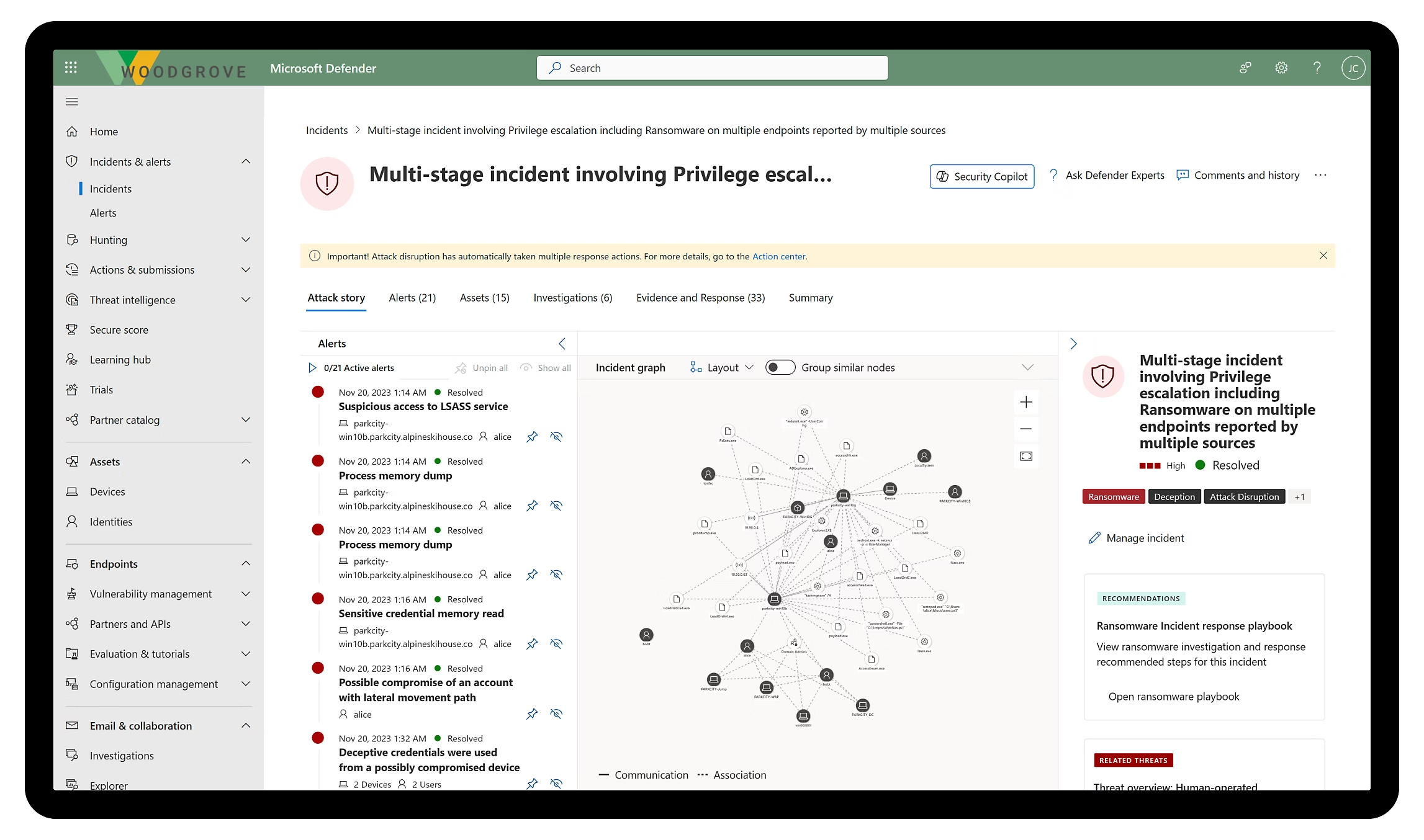
Automatically disrupt ransomware cyberattacks by blocking lateral movement and remote encryption in a decentralized way across all your devices.
Another critical component of Microsoft’s AI-driven security strategy is Microsoft Sentinel, an advanced Security Information and Event Management (SIEM) solution. Microsoft Sentinel utilizes AI capabilities to provide real-time threat detection, analysis, and automated response. Its AI-driven analytics enable organizations to detect anomalies and potential security incidents swiftly across their network environments. Additionally, Microsoft Sentinel’s ability to correlate data from various sources helps in the early identification of multi-stage attacks, thereby enhancing overall security posture.
 Gain a bird’s eye view across your enterprise with SIEM for a modern world.
Gain a bird’s eye view across your enterprise with SIEM for a modern world.
By embedding AI at the core of its cybersecurity solutions, Microsoft is committed to delivering a robust and adaptive security ecosystem. This approach heightens threat detection and incident response capabilities and ensures continuous advancements in safeguarding sensitive data and systems against the ever-evolving cyber threat landscape. Furthermore, Microsoft's AI-powered solutions significantly improve security operations by assisting security teams in identifying threats in real time and automating routine tasks.
Protect Your Business with ProServeIT's AI-driven Alarm Guardian
Our team of security experts, powered by AI-based cybersecurity technology from Microsoft, brings you Alarm Guardian security managed services. This advanced solution helps businesses detect cyber threats early and mitigate incidents such as hacking, ransomware, and data breaches around the clock. Our approach is straightforward yet powerful: Detect threats early. Respond effectively. Take the intelligent step towards Alarm Guardian.

💾 Step 1. Installation and Collection of Internal Data
The first step integrates data connectors to Alarm Guardian for efficient data gathering from various sources, laying the foundation for monitoring and analysis using Microsoft or Third-Party Connectors.
🧑🏾💻 Step 2. Detect Suspicious Threats
Alarm Guardian uses advanced analytic rules, including AI-guided Fusion, Machine Learning Behavior Analytics, Microsoft Security, and Scheduled Queries, to continuously scan for and provide alerts on potential security incidents.
🔎 Step 3. Investigate Identified Threats
Upon detecting a security incident, the service investigates the threat's scope, severity, and root cause to strategize and implement necessary risk mitigation and prevention measures.
🛡️ Step 4. Respond to Cybersecurity Threats
In the final step, Alarm Guardian automates workflows by creating "playbooks" using logic apps to mitigate threats swiftly during a security incident.
Leverage Microsoft's AI technology and our cybersecurity experts to protect your business from hackers and data breaches. Ensure proper security for your data and technology with Alarm Guardian and focus on your business. Secure your future with our expert guidance.
Related blog:
💡 Four Effective Strategies to Safeguard Your Digital Assets
🛡️ Protect Your Digital Assets with a Managed Cybersecurity Solution
Ready to boost your cybersecurity with AI?
ROM Enhanced Cybersecurity with Cybersecurity Alarm Guardian
The Royal Ontario Museum (ROM) in Toronto faced persistent global cyberattacks, highlighting key vulnerabilities in its security. ProServeIT's Complimentary Threat Landscape Review identified these threats, leading to the implementation of Alarm Guardian, a secure subscription-based service built on Microsoft Sentinel.
Alarm Guardian provides 24/7 monitoring, detection, and alerting of security threats, proactive threat hunting and automated response playbooks. The ROM now benefits from enhanced security management, threat intelligence, and comprehensive insight into its security landscape, allowing swift detection and mitigation of threats. As a result, the ROM's security posture has dramatically improved, safeguarding its valuable assets. Learn more about how ROM protected its digital assets using Alarm Guardian here.
Conclusion
The integration of AI in cybersecurity presents a dual-edged sword of benefits and challenges. While AI-powered solutions boost the capabilities of threat detection and incident response, they also create new opportunities for sophisticated cyber attacks. Despite these potential pitfalls, Microsoft's dedication to advancing AI technology guarantees robust protection for organizations across various industries. AI's prowess is harnessed using tools like Microsoft Defender for Endpoint and Microsoft Sentinel to provide comprehensive cybersecurity strategies.
Utilizing Microsoft AI technology, ProServeIT offers managed cybersecurity services through Alarm Guardian. This innovative solution empowers businesses to proactively address risks like hacking, ransomware, and data breaches by enabling early threat detection, swift responses, and continuous monitoring. Contact us today to safeguard your business, allowing you to focus on what you do best. Secure your digital assets with Alarm Guardian and confidently navigate the intricacies of the cyber threat landscape.
Tags:
.webp?width=120&height=120&name=Hyun%20Blog%20(1).webp)
July 16, 2024
.png?width=1897&height=487&name=AI-Driven%20Security%20for%20Defense%20Fortifying%20the%20Cybersecurity%20Barrier%20(1).png)

.png?width=500&height=500&name=cyber%20security_110110543%20%5BConverted%5D%20(3).png)



Comments