What Is IT Security & Why It Matters More Than Ever
In today's increasingly connected world, what’s keeping your organization’s sensitive information safe from cybercriminals? With cyberattacks growing more frequent and sophisticated, businesses must think beyond traditional defenses. A robust cybersecurity framework is essential to safeguarding digital assets, maintaining regulatory compliance, and preserving customer trust.
From ransomware to phishing to insider threats, the cybersecurity landscape is constantly evolving. In 2024, the average cost of a data breach hit $4.88 million (IBM), a sobering reminder of what’s at stake. Organizations need a multi-layered approach that combines advanced threat detection, access controls, and intelligent automation to stay ahead of attackers.
This guide explores:
🔒 Why Cybersecurity Must be a Strategic Priority
⚠️ Common Vulnerabilities and Attack Vectors
🧠 Data Encryption Best Practices (and where they fit)
🛠️ Tools That Reinforce a Cybersecurity-first Approach
🤖 The Future of Cybersecurity: AI, Automation, and Continuous Adaptation
Why Cybersecurity Must Be a Strategic Priority
Cybersecurity is no longer just an IT concern—it’s a business imperative. Whether you’re in healthcare, finance, retail, or any data-driven industry, the risks are real: regulatory fines, operational downtime, IP theft, and reputational damage.
Hybrid work, cloud-first adoption, and the use of connected devices have introduced new complexities into IT environments. According to SolarWinds, 49% of tech professionals report increased complexity due to hybrid IT, with only 8% feeling confident in managing it. That complexity often leads to security gaps.
To combat modern threats, organizations must:
- Implement real-time threat detection
- Use role-based access controls
- Regularly patch vulnerabilities
- Conduct continuous employee security training
- Adopt layered security architectures

Common Vulnerabilities and Attack Vectors
Understanding where threats originate is key to protecting your systems. Common risks include:
- Phishing & Social Engineering: 60% of breaches involve a human element (Verizon DBIR 2025).
- Credential Theft: Stolen credentials from dark web exposure remain a top attack vector.
- Unpatched Systems: Vulnerabilities like the one exploited in the 2023 MOVEit breach can lead to massive data exposure.
- Misconfigured Cloud Services: Improper settings can expose sensitive data to the public.
Cybersecurity strategies must address both external threats and internal weaknesses.
Data Encryption: A Critical Security Layer
Encryption is your last and most powerful line of defense. Even if systems are breached, strong encryption ensures stolen data is unreadable without proper keys.
However, encryption alone isn’t enough. To be effective, encryption must be integrated with broader cybersecurity strategies, including:
- Encrypting both data at rest and in transit
- Implementing strong key management (secure storage, rotation, role-based access)
- Ensuring compliance with data protection standards like HIPAA, GDPR, and PCI-DSS
According to Thales (2023), only 45% of sensitive cloud data is encrypted—a critical gap in protection. Encouragingly, that’s starting to change. Apricorn’s 2024 survey shows that 46% of organizations now require full encryption by default, up from just 23% in 2023.
To support this shift, it’s essential to choose a technology platform that provides automatic, built-in encryption capabilities. Solutions like Microsoft 365 and Azure offer encryption at rest and in transit by default, along with centralized key management. Platforms such as Google Workspace and AWS Key Management Service (KMS) also include automatic encryption features. These technologies help reduce human error and ensure consistent data protection across your environment.
Tools That Reinforce Cybersecurity
To build a truly secure digital environment, organizations need more than just strong encryption—they need a full ecosystem of cybersecurity tools working together.
Effective cybersecurity depends on a layered approach. Here are tools and technologies that enhance your encryption and overall protection strategy:
- Managed Detection and Response (MDR): Adds real-time monitoring, human threat hunting, and AI-driven analysis to detect advanced threats
- Endpoint Protection: Stops malware before it can bypass encryption or move laterally.
- Cloud Security Posture Management (CSPM): Finds misconfigured cloud assets that may expose unencrypted or sensitive data.
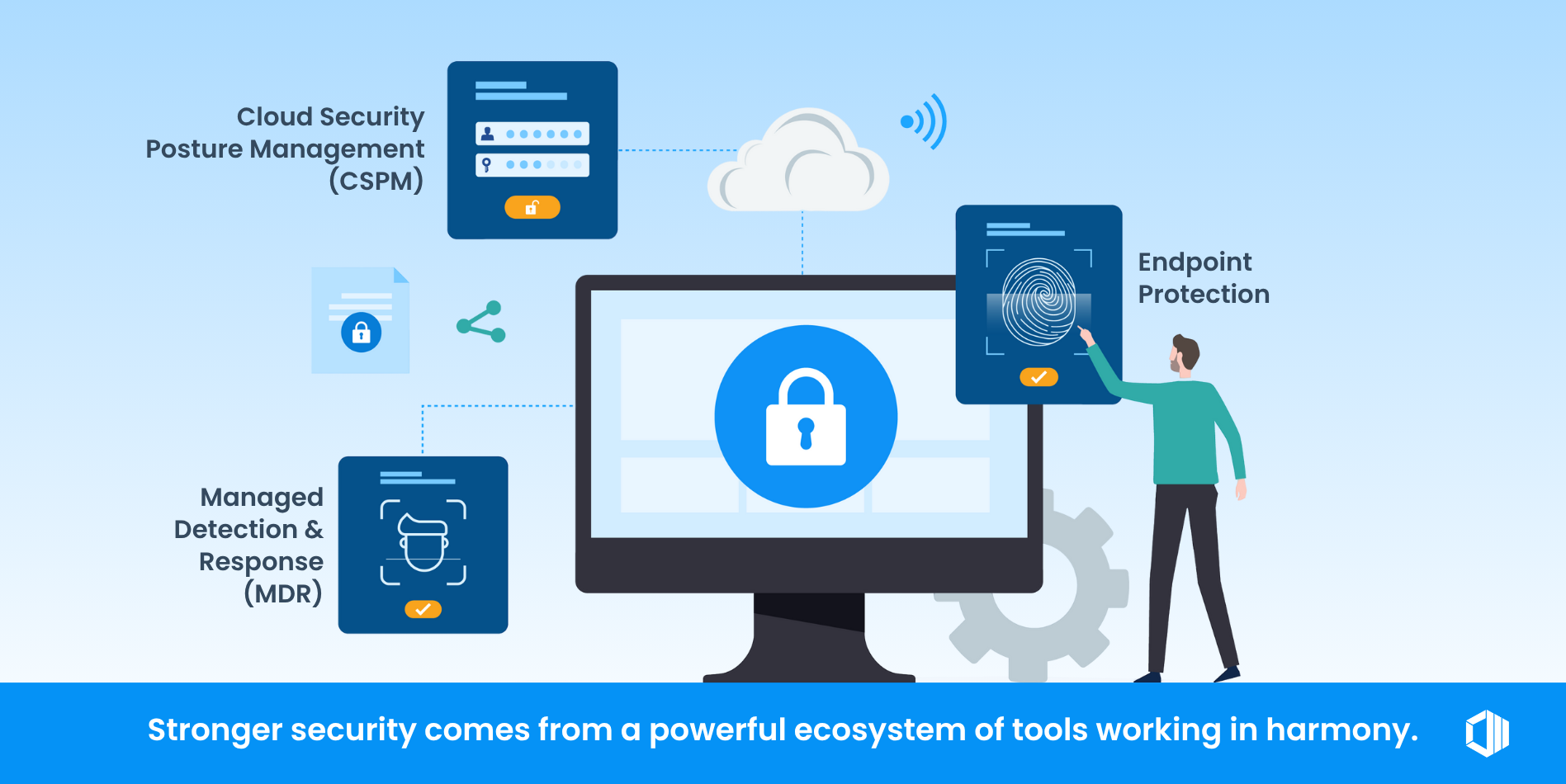
At ProServeIT, we help clients pair encryption with broader cybersecurity solutions that drive both business value and resilience. Whether you're evaluating managed services, upgrading your Microsoft environment, or developing a custom solution, we make sure security is integrated at every layer to help you stay ahead of evolving threats.
Alarm Guardian: ProServeIT’s Managed XDR Solution
ProServeIT’s Alarm Guardian is a fully managed extended detection and response (MXDR) platform that integrates seamlessly into your cybersecurity stack. It strengthens data protection by:
- Providing centralized visibility into encrypted/unencrypted traffic
- Offering automated compliance alignment with industry standards
- Integrating with Microsoft 365 and Microsoft Purview for secure collaboration
- Delivering real-time alerts and response capabilities to isolate and mitigate threats
With Alarm Guardian, encryption becomes a living part of your security infrastructure, not just a technical afterthought.
🛡️ Secure more. Worry less.
Alarm Guardian strengthens your entire cybersecurity posture with end-to-end visibility, Microsoft integration, and automated compliance.
All fully managed—so you can focus on what matters most: running your business.
The Future of Cybersecurity: AI, Automation, and Adaptability
AI is transforming how businesses approach cybersecurity. Today’s tools can:
- Detect suspicious behavior in real-time
- Automate policy adjustments
- Accelerate incident response
- Reduce manual oversight while increasing protection
Tools like Microsoft 365 Copilot bring AI-powered assistance into day-to-day business operations, ensuring that security and productivity go hand in hand.
Organizations integrating AI into their cybersecurity strategies are better equipped to face evolving threats and adapt faster to change.
Take Action: Strengthen Your Cybersecurity Framework
Cybersecurity can no longer be reactive. To build resilience, organizations must start by auditing their current security posture to understand their vulnerabilities and strengths. From there, they should implement strong encryption policies that safeguard data both at rest and in transit. It’s equally important to layer tools that support detection, prevention, and response in order to create a comprehensive defense system. Finally, aligning IT operations with overall business strategy ensures that security efforts support long-term goals and operational efficiency.
Whether you’re modernizing your infrastructure or developing a cybersecurity roadmap, ProServeIT is here to help. Our team can guide you through the complexities of encryption, compliance, managed detection and response, and Microsoft integration.
👉 Contact us today to future-proof your cybersecurity with a smart, scalable, and secure foundation.
Tags:

June 05, 2025

.png?width=500&height=500&name=cyber%20security_110110543%20%5BConverted%5D%20(3).png)


Comments