What Is IT Security & Why It Matters More Than Ever
In an era where data all around the world lives digitally, an organization's digital assets are some of its most crucial possessions. As security software advances in complexity, data breaches and social engineering evolve with equal sophistication.
However, did you know that not all data breaches are a result of hacking? Some, like social engineering, don't require any advanced technical skills. Instead, they rely on manipulating human behavior and emotions to gain unauthorized access to sensitive information. Ranging from customer or client details to employee records to even confidential data, social engineering attacks can compromise it all, doing serious damage to a company's reputation and workflow.
While busy schedules bog professionals down with little time to identify to these often-imperceptible threats, it is more important than ever to understand how to identify and take the right measures against them. So, the question remains: how can you protect yourself from social engineering?
This blog serves as a comprehensive guide to understanding what social engineering is, how attacks are carried out, and what the best countermeasures are against them. Additionally, we explore ways in which ProServeIT can help strengthen your company's security posture to prevent any potential malicious attacks. Let's dive in.
Jump to a section:
🔓 Understanding Social Engineering
⚔️ Effective Countermeasures Against Social Engineering Attacks
✋ Quick Tips to Prevent Social Engineering Attacks
⛓️ Advanced Prevention Techniques
Understanding Social Engineering
You may have seen it, heard about it, or even experienced it. Now, it's time to understand it. Here's a breakdown of social engineering, why it is important to pay attention to and the most common ways in which it is conducted.
What is Social Engineering?
Ever received a suspicious email from an external source pretending to be someone from your company's IT department? That's basic social engineering.
Social engineering is a manipulation technique that involves using psychological tactics to influence people into revealing or providing access to critical information.
Simply put, it exploits human trust and vulnerability to gain an entry point into buildings, systems, or data. The objective is to "trick" individuals into divulging sensitive information rather than using software or hacking strategies.
Social engineers meticulously craft scenarios where they deceive people into breaking normal security procedures or best practices.
At this point, you may be wondering, "Is phishing social engineering?", "Is it really that common?" or "Just how many social engineering tactics exist?". Let's explore the answers to all these questions below.

Why Should You Be Concerned About Social Engineering?
Social engineering is a low-cost method that can yield substantial results for hackers looking to disrupt an organization or steal its information.
In fact, this tactic is so commonplace that 98% of cyber-attacks involve social engineering to some degree.
Not just that, but these attacks are on the rise. According to a 2024 article, the US Government's The Health Sector Cybersecurity Coordination Center has warned that "hackers are targeting IT help desks in the health sector with advanced social engineering tactics."
Small businesses seemingly need to exercise the greatest amount of caution. A study by Barracuda revealed that employees of small businesses, with fewer than 100 workers, are subjected to social engineering attacks at a rate 350% higher than their counterparts in larger enterprises.
The impact of successful social engineering campaigns can be devastating. IBM's 2023 Cost of a Data Breach report highlights that global data breach costs averaged out at $4.3 million per incident. Indeed, organizations that extensively incorporated security AI and automation experienced nearly $1.8 million less in data breach costs compared to those that did not utilize these technologies, marking the most significant cost-saving measure reported.
 For all organizations, big or small, it is imperative to understand the existing threat landscape before taking proactive steps to combat the threats. Let's delve deeper into the different types of social engineering attacks that are commonly used by hackers.
For all organizations, big or small, it is imperative to understand the existing threat landscape before taking proactive steps to combat the threats. Let's delve deeper into the different types of social engineering attacks that are commonly used by hackers.
7 Common Types of Social Engineering Attacks
Social engineering is a highly versatile form of attack, with several techniques and methods being used by cybercriminals to deceive victims. Below are seven of the most commonly used types of social engineering attacks.

1. Phishing
Phishing is a scam to steal personal information like usernames and credit card numbers, usually through fake emails or websites pretending to be trusted organizations. Attackers trick people into sharing sensitive details or clicking on harmful links.
For example, imagine receiving a fake email from your IT department requesting your login credentials to fix an urgent issue with your account. You unknowingly provide your sensitive information, which the attacker can then use to gain access to your account and potentially steal your data. Scary, right?
Phishing is one of the most common social engineering attacks. In 2023, nearly six in ten employee-reported suspicious emails had the intention of credential theft according to Statista.
2. Spear Phishing
Spear phishing is a highly targeted form of phishing that focuses on specific individuals - especially individuals in positions of authority - or organizations. The attacker may gather personal information about the victim to create a more personalized and convincing message, making it harder for them to detect that it's a fraudulent attempt.
3. Pretexting
Pretexting involves attackers using made-up scenarios to trick someone into giving away sensitive information, often by pretending to be someone else or using a fake story to gain trust.
For example, if you receive a call from someone claiming to be a researcher conducting a survey on behalf of your bank, asking for your account details to verify your participation in the study. This scenario could be a pretext, where divulging your account details could lead to unfortunate consequences.
Contrary to phishing, which leverages the target's immediate emotional reaction through urgent calls-to-action, pretexting involves the gradual building of trust. It uses elaborate and convincing narratives to justify the solicitation of sensitive information.
4. Baiting
Baiting involves tricking someone with a tempting offer, like a free download, to steal personal information. It often uses a USB drive or a malicious link, risking malware infection.
For example, an attacker may leave USB drives labeled "Employee Bonuses 2024" in a public place where employees of a targeted organization might find them. If someone were to plug one of these drives into their work computer out of curiosity, it could compromise the entire network.
5. Tailgating
Tailgating is when an unauthorized person gains physical access to a restricted area by following someone with legitimate access.
For example, if an attacker were trying to gain access to a secure server room, they may wait outside until an authorized employee enters and then follow closely behind them before the door locks.
6. Quid Pro Quo
Quid pro quo is when an attacker offers a freebie or something of value in exchange for personal information or access.
For instance, a supposed software vendor might contact you, suggesting that your organization has been chosen for a "free" audit service to enhance system efficiency. To begin this audit, they might ask for remote access credentials, which could potentially be exploited for malicious purposes.
While baiting relies on the greed of an individual, quid pro quo leverages their desire for a perceived benefit or reward.
7. Scareware
Scareware is a type of malware that scares users into purchasing fake antivirus software by claiming their device is infected with a virus. It typically comes in the form of pop-ups or ads, prompting the user to take immediate action.
Effective Countermeasures Against Social Engineering Attacks
As we can see, social engineering attacks take on many forms and are highly adaptable to exploit human vulnerabilities. So, what can organizations and their employees do to protect themselves?
.png?width=1897&height=950&name=8%20Social%20Engineering%20Countermeasures%20(1).png)
8 Best Social Engineering Countermeasures
What is the best countermeasure against social engineering? There isn't one because it requires many strategies that work together to achieve the strongest protection against these attacks.
1. Get Educated
The first and most important defense against social engineering is knowing what it is and how to deal with it. Staying up to date on the latest social engineering attacks is necessary to recognizing potential threats and taking appropriate action. For organizations, providing employee training in this aspect is critical.
2. Implement Multi-Factor Authentication
Multi-factor authentication (MFA) adds an extra layer of protection against unauthorized access. By requiring multiple forms of identification, such as a password and biometric verification, MFA makes it harder for attackers to gain access even if they have obtained login credentials.
3. Verify Requests
Whenever someone requests sensitive information, always verify their identity and the legitimacy of the request before sharing any details. This includes calls, emails, and even in-person interactions. If possible, use a different channel to contact the person or organization directly.
For example, if you receive an urgent request from your bank, don't reply or click links; contact them using official channels. For unexpected calls, verify the caller's identity and follow up with the organization through verified means, ensuring you're dealing with the legitimate entity.
4. Use Anti-Spam Filters
Anti-spam filters can help identify and block phishing emails by analyzing their content and sender information. These filters are also effective in detecting other forms of social engineering attempts, such as pretexting and quid pro quo.
5. Robust Firewall and Antivirus Protection
A secure firewall can prevent unauthorized network traffic and block malicious attempts to access sensitive information. Antivirus software is essential in detecting and removing malware, including scareware and other types of malicious software used in social engineering attacks.
6. Regularly Update Systems
Keeping systems, like firewalls and antivirus protectors, up to date with the latest security patches can prevent attackers from exploiting vulnerabilities through malware or other malicious means.
7. Penetration Testing
Regularly conducting penetration testing or pen-testing, or simulated social engineering attacks, can help expose weaknesses in an organization's security protocols and employee awareness. This practice allows organizations to identify potential vulnerabilities and take action to mitigate them before real attackers can exploit them.
8. Check for SSL Certificates
SSL (Secure Sockets Layer) certificates are essential for secure communication and help to verify the authenticity of a website. If the website's URL begins with "https://" instead of "http://", it is secured with an SSL certificate. Another way is to look for the SSL padlock icon in the web browser URL bar before entering sensitive information, as it indicates that the connection between your device and the website is secure.
Are you concerned about the rising threat of social engineering attacks on your business?
At ProServeIT, we specialize in fortifying your digital defenses against sophisticated social engineering tactics.
If protecting your company’s sensitive data from cunning cyber threats sounds like a priority, let’s talk.
Recognizing and Reporting Suspicious Activity
Identifying social engineering attempts is the key to preventing them. Here are some telltale signs:
🚀 Urgency: Attackers often create a sense of urgency to pressure individuals into making impulsive decisions. Look out for emails or requests that require "immediate action" or are labelled "urgent".
🙍 Request for personal information: Be cautious when asked for sensitive or personal information, like login credentials, bank details, identification details, especially if it's unexpected.
🎁 Unusual offers or requests: Offers that sound too good to be true or requests that seem out of the ordinary should raise red flags. Furthermore, receiving an odd request from a colleague or peer could signal that their account has been compromised, or that an impostor is attempting to mimic their identity.
❓ Questionable email address or website: Attackers frequently employ an email address or create a website that looks very similar to that of a well-known company, with slight modifications or character omissions to ID or URL. For example, instead of "paypal.com", an attacker's website might be "paypall.com".
👋 Generic greetings: Using non-personal greetings like "Dear Valued Customer" or "Sir/Ma'am" and not including contact details in the signature point towards a phishing attempt.
🔗 Fake hyperlinks and websites: When you hover over links in an email and the displayed text doesn't match the actual link, it could be a sign of spoofing. Attackers might also use URL shorteners to conceal the real link destination.
🔤 Poor grammar: Typos, spacing errors, inconsistent sentences and formatting are markers of a potential social engineering attempt.
📩 Questionable attachments: Unsolicited emails urging users to download and open attachments often serve as a method for spreading malware.

Having explored methods to recognize social engineering tactics, let's delve into the procedures for reporting such incidents:
📞 Call your IT department: In an organizational setting, if you think an email or request is suspicious, contact your IT or security team. They can verify the legitimacy of the request and take appropriate action.
👮 Report to authorities: If you are a victim of fraud or social engineering fraud, report it to law enforcement immediately.
🏦 Confirm with your bank: For matters involving your financial information, initially reach out to your bank to confirm any dubious activities. Following that, consider closing any accounts that might have been jeopardized.
Quick Tips to Prevent Social Engineering Attacks
Social engineering attacks can happen to anyone, but there are steps you can take to minimize their chances of success.
How to Enhance Your Security Posture
A key aspect of bolstering your defenses involves learning how to prevent social engineering attacks by adhering to some effective best practices.
Personal Security Practices
🐌 Go slow: Take your time to evaluate any requests or communication, especially the ones that put you under pressure. Remember, scammers will often try to persuade you into making quick decisions.
💪 Use strong passwords: Use unique and complex passwords for all accounts and change them regularly. Password managers can help create and store secure passwords.
📱 Be cautious on social media: Attackers can use information shared on social media to craft personalized phishing emails. Be mindful of what you post publicly, and limit access to your personal information.
⚠️ Don't trust unsolicited emails or calls: Never open attachments or click on links in unsolicited emails. Similarly, don't trust unexpected phone calls requesting personal information. Always think twice about whether a request is realistic or not, and whether its sender would make such requests in the first place.
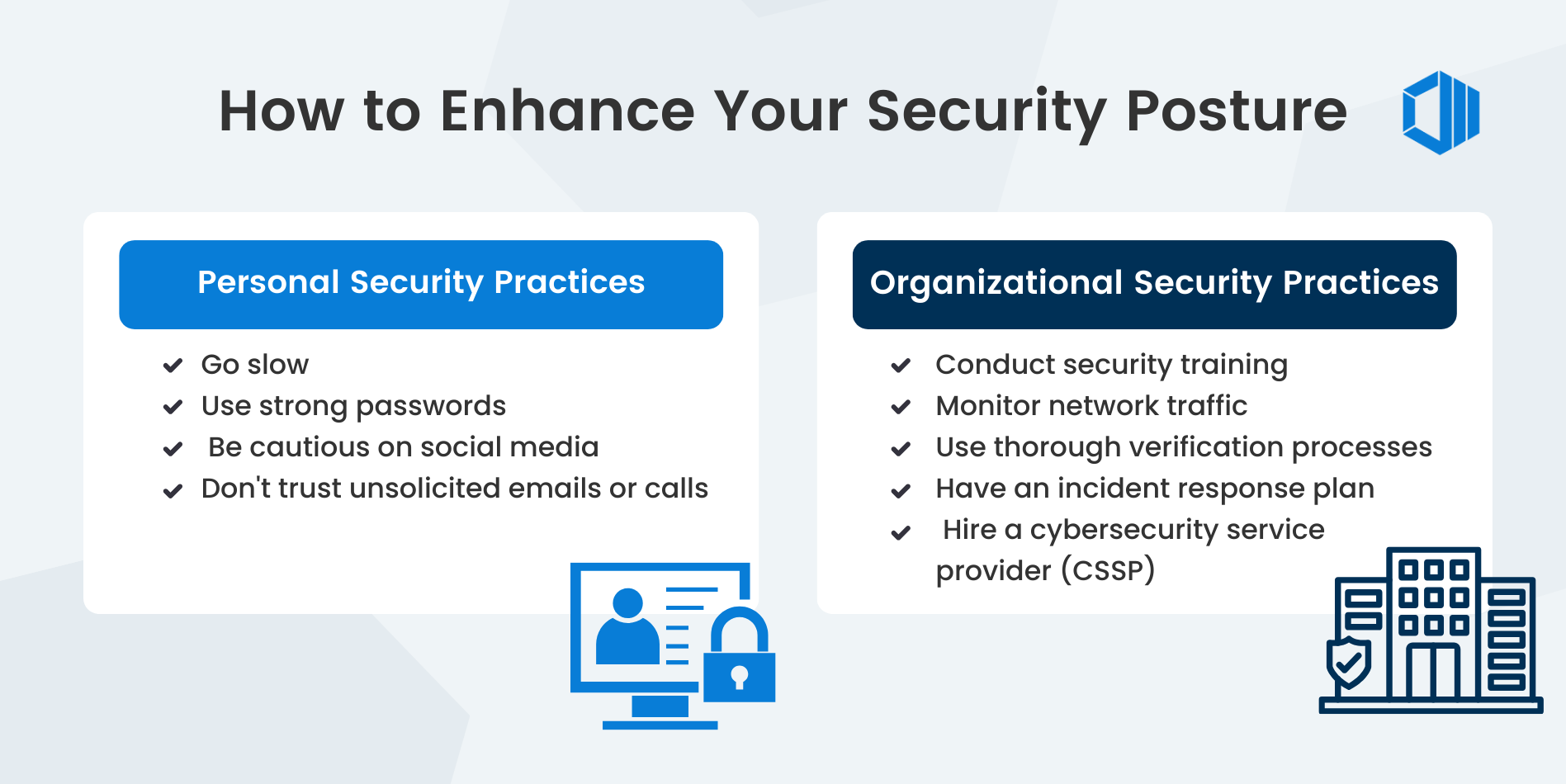
Organizational Security Practices
👩🏫 Conduct security training: Educate employees about social engineering threats and how to identify and report them.
🔎 Monitor network traffic: Employing a network monitoring system can help identify suspicious traffic or unusual behavior that could indicate a social engineering attack.
🔂 Use thorough verification processes: Set up checks for changes to suppliers, vendors, and financial details to ensure their authenticity before any issues arise.
⛔ Limit Access: Limit access to sensitive information and systems only to those who require it for their job. This minimizes the risk of internal attacks or data breaches.
💡 Have an incident response plan: In the unfortunate event of a social engineering attack, having a well-defined plan can help mitigate its impact and prevent further damage. Consider implementing an alternative method for reporting incidents, especially in scenarios where employee emails may be compromised.
✅ Hire a cybersecurity service provider (CSSP): A cybersecurity service provider (CSSP) can help identify vulnerabilities, implement security measures, and provide ongoing monitoring and support to prevent social engineering attacks. Many organizations have turned to CSSPs and their profound expertise since such customized and tailored solutions provide enhanced and long-term security, allowing companies to function with greater peace of mind on a regular basis.
One such reputed CSSP is ProServeIT with their own Alarm Guardian service. Offering real-time monitoring, detection, and response, Alarm Guardian employs a proactive approach against hackers. Powered by AI-based cybersecurity technology from Microsoft and a team of highly trained and skilled cybersecurity experts, ProServeIT's unparalleled managed security solution can play a crucial role in protecting your digital assets. By collecting information about potential threats, identifying risk areas where security can be strengthened, offering round-the-clock surveillance and ensuring that an organization's security practices meet compliance standards, our Alarm Guardian service provides all-round protection against social engineering attacks.
Learn more about organizational Cybersecurity Solutions.

Digital Hygiene and Safe Browsing Practices
In addition to best practices from a social engineering standpoint, here are some general tips to ensure your time on the internet is as safe as can be:
🔒 Use a Virtual Private Network (VPN): A VPN encrypts your internet connection and protects your online activities from hackers or prying eyes on public Wi-Fi networks.
👨💻 Use caution with public Wi-Fi: Avoid conducting sensitive transactions, such as online banking, on public Wi-Fi networks.
🍪 Clear your browsing history and cookies: Regularly clearing your browser history and cookies can help prevent tracking by third-party websites.
🖥️ Regularly monitor your online accounts: Keep an eye out for any unfamiliar activity on your accounts and report it immediately if you suspect fraudulent access. Remember to use different passwords for different accounts.
Advanced Prevention Techniques
While implementing the above-mentioned practices can be critical in safeguarding against social engineering attacks, there are also more advanced techniques that you can consider.
Technological Tools and Solutions
Other than employing MFA (multi-factor authentication), enabling spam filters, encryption and firewalls, here are the ultimate solutions on how to stop social engineering attacks:
Secure Email Gateways (SEGs)
SEGs filter emails through multiple layers of protection, including scanning for malicious attachments and links.
Intelligent Security Management
Employing AI-based security software in combination with a team of cybersecurity experts is the most robust form of protection against social engineering. ProServeIT's Alarm Guardian service does just that. Utilizing the AI-powered capabilities of Microsoft Sentinel and backed by a team of expert cybersecurity professionals, our Alarm Guardian managed security service provides businesses with the ability to quickly detect cyber threats and effectively respond to incidents like hacking, ransomware, and data breaches, ensuring 24/7 protection. Learn more about Alarm Guardian.
Developing a Security-Focused Culture
Ultimately, the most effective way to prevent social engineering attacks is by creating a security-focused culture within your organization. This means not only implementing technological solutions but also educating and training employees on cybersecurity best practices regularly. It also involves fostering an environment where employees feel comfortable reporting suspicious activity and taking steps to continuously improve your organization's security posture.
Research highlighted in ScienceDirect examined the effectiveness of various cybersecurity training programs, revealing beneficial outcomes from the sessions. Additionally, a 2023 Forbes article highlighted that "cybersecurity risk can be reduced from 60% to as low as 10% with a good training program."
By working together, educating ourselves and staying vigilant, we can all play a role in preventing social engineering attacks and safeguarding against cyber threats. After all, maintaining an organization's security is the responsibility of every employee.
Conclusion
To prevent social engineering attacks, a combination of countermeasures and safe practices is crucial for both, individuals and organizations. Asking the right questions, staying alert, and constantly updating security protocols can significantly reduce risks. Ultimately, being proactive is the best form of action against these threats. For organizations, amidst increasingly sophisticated cybersecurity challenges, consulting with experts is the need of the hour. To that end, ProServeIT is here to help.
Stay Ahead of Social Engineering Attacks with ProServeIT's Alarm Guardian Managed Security Solution
As an esteemed member of the Microsoft's Intelligent Security Association (MISA) and a distinguished provider within the Managed Security Solutions Provider (MSSP) program, ProServeIT has earned recognition for its superior expertise and advanced qualifications in cybersecurity solutions. Through this partnership with Microsoft's security technology, Alarm Guardian incorporates the most advanced, cutting-edge security measures to protect against the ever-changing threats of cyber-attacks and data breaches.

This modern managed security solution:
✅ Provides installation of your new digital "security system" to safeguard your digital assets.
✅ Actively monitors incoming alerts in your environment, effectively distinguishing between false alarms and real threats.
✅ Identifies areas in need of additional protection and proactively fills any cybersecurity gaps.
✅ Delivers contextual insights to enhance the security of all your digital assets.
Visit our Alarm Guardian offer page for more information on the three levels of protection we offer for your organization. Don't hesitate to contact us to discuss your organization's specific needs.
Tags:

May 03, 2024

.png?width=500&height=500&name=cyber%20security_110110543%20%5BConverted%5D%20(3).png)



Comments