As the world continues to digitize, cybersecurity has become an increasingly important issue for businesses. With cybercrime on the rise and hackers becoming more sophisticated with every passing year, it is essential for companies to be vigilant in protecting their digital assets.
Cybersecurity threats are expected to reach epidemic proportions, leaving many companies vulnerable unless they take proactive measures now to protect their digital assets from cybercrime. Companies must remain vigilant and understand the risks associated with cybersecurity breaches in order to remain competitive.
By regularly updating software and systems, encrypting data and other sensitive information, utilizing two-factor authentication, conducting cybersecurity audits, investing in technology solutions, and creating a cybersecurity incident response plan, companies can safeguard their digital assets and keep their company safe.
This blog post will explore the state of cybersecurity in 2022 and discuss how businesses can protect themselves from cybercrime in the future. Keep reading to learn more!
In this blog you will find:
The Impact of Cybercrime on Businesses
What Steps Companies Can Take to Safeguard Their Digital Assets
Technology Solutions to Enhance Your Cybersecurity
Learn more about Cybersecurity
Conclusion
-
The Impact of Cybercrime on Businesses
The impact of cybercrime on businesses cannot be overstated. In 2022, the cost of cybersecurity breaches is estimated to reach $6 billion, with companies losing an average of $3 million per attack. Not only do these breaches cost companies money, but they can also have a long-term impact on their reputation and customer trust.
“Attackers are adapting and finding new ways to implement their techniques, increasing the complexity of how and where they host campaign operation infrastructure,” says Amy Hogan-Burney, General Manager in the Digital Crimes Unit at Microsoft.
The increasing sophistication of cybercriminals will make it more difficult for companies to protect themselves from data breaches and other threats in the future. According to a report by Microsoft, individuals who operate in the cybercrime industry have become more organized in order to target larger companies for immense profit.
Ransomware attacks are one of several methods used by cybercriminals to infiltrate a company’s technology environment and lock access to key systems until they receive a specified sum from the company (sometimes a ransom can be in the millions of dollars). Such attacks present an increased danger to industries, governments, and essential infrastructure which are targeted by criminals in the “growing cybercriminal ecosystem”.
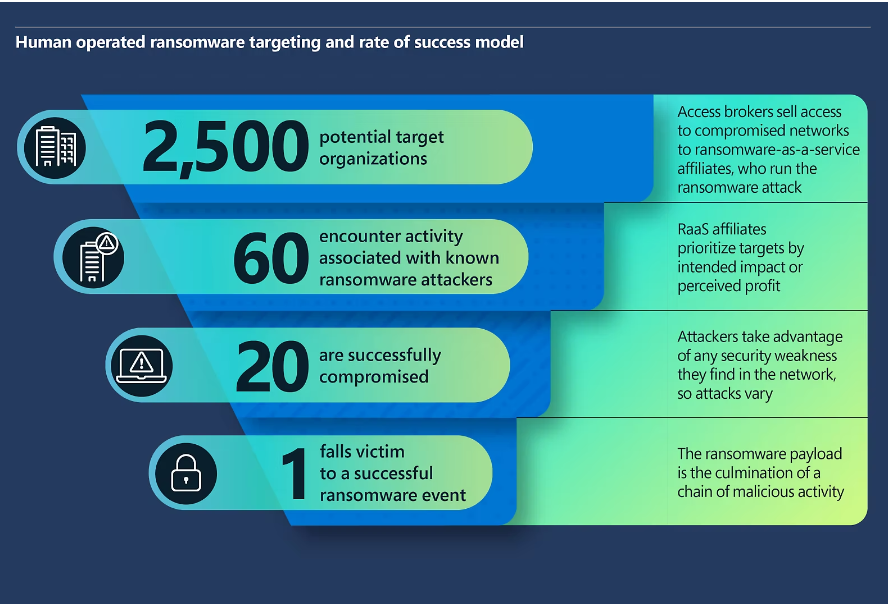 Infographic of a human operated ransomware targeting and rate of success model. Graphic was created by Microsoft Security.
Infographic of a human operated ransomware targeting and rate of success model. Graphic was created by Microsoft Security.
There are several factors that can make an organization susceptible to a ransomware attack. Microsoft did a study and compiled the top findings among ransomware incident response engagements. They are stated below from most common across organizations to least common:
1) Insufficient privilege access and lateral movement controls (93%)
2) Limited adoption of modern security frameworks (87%)
3) Insecure configuration of identity provider (86%)
4) Insufficient application security practices (74%)
5) No multifactor authentication (74%)
6) Lack of information protection control (65%)
7) Low maturity security operations (62%)
The top reason mentioned about is important to note as the definition of lateral movement (from the context of cybersecurity) highlights the end goal and strategic focus of a cyber attacker when the individual gains access to your technology environment. According to Crowdstrike, “lateral movement refers to the techniques that a cyber attacker uses, after gaining initial access, to move deeper into a network in search of sensitive data and other high-value assets”. Sometimes, attackers can gain access through something as simple and innocuous as an email from your manager.
Business emails are another point of entry that cybercriminals can use to infiltrate an organization through the deceptive practice of “phishing”. Phishing poses a significant threat to email users because of how it can impact a company based on one user’s decision to interact with a suspicious email which can target any available inbox (from a frontline worker to the CFO). Such incidents are growing (in terms of volume) across businesses around the world.
In the ring chart below, Microsoft gathered data on how business emails are compromised and the date range for this study was from January to June 2022. The data on this chart highlights just how often such phishing attacks occur and which one is the most popular (based on its effectiveness from a cybercriminal’s perspective).
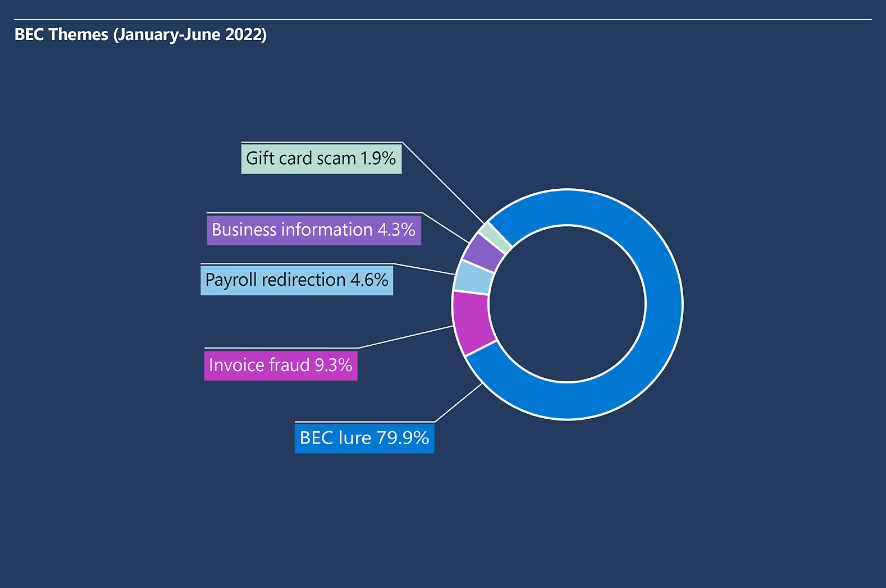 Chart of business email compromise (BEC) themes by percentage of occurrence. Graphic was created by Microsoft Security.
Chart of business email compromise (BEC) themes by percentage of occurrence. Graphic was created by Microsoft Security.
What Steps Can Companies Can Take to Safeguard Their Digital Assets?
To protect their digital assets, companies can take a number of proactive steps rather than wait for an incident to occur. These include regularly updating software and systems, encrypting data and other sensitive information, utilizing two-factor authentication whenever possible, and conducting regular cybersecurity audits. Additionally, companies should create a cybersecurity incident response plan to ensure they are prepared in the event of an attack.
Here are a few proactive steps that Microsoft recommends for a healthy defense against ransomware attacks:
📄 Audit credential exposure.
⚠️ Reduce security operation centre (SOC) alert fatigue by hardening your network to reduce volume and preserve bandwidth for high priority incidents.
☁️ Prioritize cloud hardening.
⬇️ Reduce the attack surface.
🌐 Harden internet-facing assets and understand your perimeter.
Here are a few proactive steps that Microsoft recommends for a healthy defense against phishing attacks:
⚙️ Configure Domain Keys Identified Mail (DKIM) and Domain-based Message Authentication Reporting & Conformance (DMARC) action policies to prevent delivery of non-authenticated emails that might be spoofing reputable senders.
🤖 Use a machine-learning based security solution that quarantines high probability phish and detonates URLs and attachments in a sandbox before the email reaches the inbox, such as provided by Microsoft Defender for Office 365.
🔒 Enable impersonation and spoofing protection features across your organization.
📋 Audit tenant and user created allow rules and remove broad domain and IP based exceptions. These rules often take precedence and can allow known malicious emails through email filtering.
🪝 Regularly run phishing simulators to gauge the potential risk across your organization and to identify and educate vulnerable users.
Here are a few proactive steps that Microsoft recommends for a healthy defense against infrastructure attacks:
☑️ Conduct regular automated user activity anomaly checks through detections at scale to help reduce these types of attacks.
🛡️ Implement good cyber hygiene and provide cybersecurity training for employees with guidance for avoiding being manipulated by socially engineered messages.
📶 Update and secure routers on corporate and private networks.
Technology Solutions to Enhance Your Cybersecurity
In addition to following cybersecurity best practices, companies should also invest in technology solutions that will help enhance security. These include firewalls and other network protection measures, intrusion detection systems, and endpoint security solutions.
Additionally, artificial intelligence (AI) is becoming increasingly important for cybersecurity, as it can identify and respond to potential threats in real time.
Microsoft has dedicated itself to helping create a safer digital ecosystem for internet users around the world. Here is how they are helping to combat cybercrime for their large global customer base:
- 70 billion email and identity threat attacks were blocked by Microsoft last year alone.
- 2.75 million site registrations were successfully blocked by Microsoft to get ahead of criminal actors that planned to use them to engage in global cybercrime.
- 531,000 unique phishing URLs and 5,400 phish kits were taken down at the direction of Microsoft’s Digital Crimes Unit.
To achieve these results, Microsoft invests more than $1 billion annually in cybersecurity research and development and employs more than 3,500 security experts dedicated to data privacy and security. By collaborating with Microsoft for their cybersecurity needs, organizations can spend more time focused on their business and less time worried about their cybersecurity.
As a Microsoft Cloud Partner, ProServeIT has the expertise and experience to assist organizations like yours to address any cybersecurity pain points and better defend your environment against future cyberattacks. With our Alarm Guardian service, you can ensure that your organization’s digital assets are protected through the use of Microsoft Sentinel. Microsoft Sentinel helps provide confidence in your defenses by alerting you when there's an abnormality and proactively taking action against potential threats before they become a bigger problem.
Here are 3 key benefits of using Alarm Guardian:
🔒 Improve your organization's overall security posture.
🚨 Keep up to date on current threats and become more proactive in your threat hunting.
⏱️ Timely response to cyber attacks before damage is done.
Interested in learning about cybersecurity from the experts? Read the next section to learn more!
Learn more about Cybersecurity for your organization
Not sure what steps you need to take to improve your organization’s cybersecurity stance? Check out our free course on Cybersecurity brought to you by our new ProServeIT Academy.
This course has 3 informative classes this semester, delivered online by our in-house Cybersecurity experts and is designed for IT leaders and professionals. See our list of classes below:
🔒 Class 01: Simplifying Your Security Journey
The journey to simplifying your security process starts with identifying your security risks and determining where you can be attacked. What could happen if your information is stolen or released? Once you’ve identified your risks, you can decide how to mitigate them and close your gaps. You may want to prioritize risks to your sensitive data or risks to your business reputation. Once you have remedied your major risks, the last step is to monitor and ensure that new evolving threats are addressed as they arise.
Cybersecurity is a continuous process and it’s never too late to get started. Learn how to deploy a simple 3-step process to start you down the path to digital security.
Register now to watch the video recording!
📋 Class 02: Microsoft's Zero Trust Model
Today’s organizations need a new security model that more effectively adapts to the complexity of the modern environment. Securing your digital assets requires Zero Trust. A Zero Trust security model treats every activity as a threat unless you can prove that it isn’t.
Start with a self-assessment to get recommendations customized for your organization. Explore methods you can use today to stop malicious activities before they can do damage. Align your Zero Trust investments to your current business needs and improve your organization’s security posture.
Register now to watch the video recording!
🛡️ Class 03: Ransomware as a Service: How to Protect Your Organization
How can you protect your organization against sophisticated nefarious activities such as theft of highly valuable data, threats to publish your data or repeated extortions for payment once a cybercriminal gets access to your environment?
Learn how you can harden your environment against ransomware threats. Reduce your attack surface by addressing security blind spots, modernizing your legacy configurations, removing easy entry points into your environment, and employing sophisticated tools that can detect and respond to imminent attacks.
Register now to watch the video recording!
Conclusion
Overall, the cost of cybercrime will only continue to increase as we become more reliant on technology. By understanding common methods used by attackers and improving your organization’s cybersecurity posture, you can help protect your business from being a victim of costly cybercrime.
Interested in enhancing your organization’s cybersecurity? Discover how our ProServeIT team can help by clicking this link today.
Tags:

December 01, 2022

Comments