Traditionally, the perimeter of your digital identity within your organization would have been the network. Everything that you wanted to protect is secured behind your firewalls. This includes all your endpoints, on-site users, servers, applications and so forth.
However, with the advancement of technology, we now use a hybrid cloud where everything is stored in a public or hybrid cloud. This allows personal devices to be used for business purposes and mobile devices as a tool to conduct business on applications. More recently, the rise of COVID-19 has pushed employees to work remotely in which your digital identity is no longer on your local network or behind your firewall. As everything becomes more cloud-based, we find ourselves increasingly using software as a service (SaaS) instead of setting up servers and physical infrastructure. This can elevate the risk of cyber threats without proper tools and processes in place.
So, the question must be asked – how do you protect your digital identity against cyberattacks? In this blog, we’re going to show you different ways to protect your identity from cybercrime.
Related Blogs
Protect Your Digital Assets with a Managed Cybersecurity Solution
What is Social Engineering & 4 Ways to Prevent Attacks
How to Protect Your Digital Identities from Cyberattacks?
As applications become more cloud-based, it is important for you to protect your identity when your organization puts its foot into the cloud. In the Microsoft world, there are plenty of tools and services that organizations can use to help protect your digital self. Here are some of the features that you can configure with Microsoft to protect these identities:
Multi-Factor Authentication (MFA) Microsoft Defender for Identity
Self Service Password Reset (SSPR) Privileged Identity Management (PIM)
Conditional Access Policies Microsoft Sentinel
Risky Users\Risky Sign-Ins Evaluation Identity Access Management (IAM)
Single Sign-On (SSO) Password Policies
These services help lower the cyber crimes within your organization and protect your digital identity.
Want to protect your digital end-users? Download this eBook(Safe Computing Best Practices for End-Users) to learn practical tips and protect your organization from a cyber-breach.
Below are some tips on how to fully optimize these features to attain maximum security.
10 Ways to Protect Your Digital Identities from Cyber Attacks
1. Multi-Factor Authentication for corporate as well as personal accounts.
📱In order to log into your accounts, you will need to use two factors to authenticate yourself. This includes either a combination of password or pin-code, biometrics like face recognition or a fingerprint, or some other method you may have.
❗Caution: protect personal accounts you have with MFA, not just corporate accounts. If you use the same credentials, hackers can attack your personal account using your corporate account.
2. Use a Password Manager.
💻 This application can help store, manage complex and unique passwords for every new service that you need. Make sure to choose a password manager that supports MFA – you don’t want to get hacked within the manager.
3. Use Passphrases, Not Passwords.
💬 A passphrase is a combination of words used as a password for your accounts.
📃 One of the most common methods is to take four words that are not associated and combine them together. For example, “whitewallbigscreen” is a passphrase. With this method, try to aim for 12-16 characters for your passphrase for additional security.
❗Caution: never use personal information in your passwords or passphrases as it gives hackers an advantage when attempting to steal your identities.
4. Always check the fine print before signing up to services.
❔Ask yourself – what permissions are we giving apps or services on social media? Social media apps are known for tracking your behavior and for accessing your list of contacts. As well, if you are using your corporate account, think about what you are allowing before signing up as hackers can request access to read and send emails on your behalf – that is often their way into the company.
5. Avoid Public Wi-Fi Networks.
📶 Public wi-fi networks are the center of cybercrime and present a serious security threat to anyone who uses a public wi-fi hotspot at airports, hotels, cafes, and restaurants. If necessary, use a VPN (virtual private network) when connecting to public wi-fi.
6. Don’t overshare personal information – be careful what personal data you put and where.
7. Always take an extra second before you click or post
📨 One of the most common phishing scams comes from cyber criminals impersonating services that you sign up for such as Netflix, Amazon, Paypal, etc. Through this, they will try and lure you by emailing you that there’s an issue with your payment or account. To be safe, take an extra second to check who the sender is.
8. Use a Single Sign-ON (SSO) platform for all business apps – this allows all staff to access all their necessary business apps with a single login.
9. Implement Access Policies – this can be used enable location-based restrictions or device restrictions to block access in certain applications. In return, this significantly helps block cyberattacks that come from outside your country.
10. Train employees about digital security.
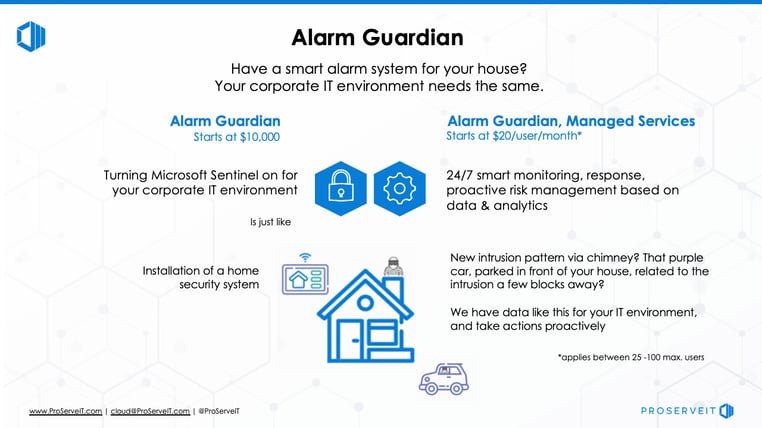
Alarm Guardian Uses Microsoft Sentinel to Protect Your Organization
As we have provided you with 10 tips to protect your identity, the next step is thinking about tools that effectively help you against cyberattacks. Microsoft Sentinel, a Cloud-native security information and event manager (SIEM) platform helps your organization to filter legitimate events happening in your network from viable threats. Learn more about Alarm Guardian.
How does Microsoft Sentinel Protect my Identity?
📈 Data collection from different sources throughout the cloud - this includes data integration with existing tools and thorough analysis of your data security environment.
- 🏗️ Built-in user and entity behavioral analytics (UEBA) help in identifying threats and their potential impacts.
- 📍 Detects suspicious behavior, compromised assets and its impact radius. With this, security teams can further prioritize their investigation and incident handling.
ProserveIT offers a solution that is built around Microsoft Sentinel called Alarm Guardian.
This service is supported by ProServeIT’s Security Operations Center’s security analysts and security engineers on a 24 x 7 x 365 basis.
⏰Alarm Guardian will provide real-time analysis and response to security generated by your servers, devices, firewalls and network device users. It is much like an alarm system that scans for suspicious activity, and alerts you to potential threats within your network.
If you are looking for ways to increase your security and protect your digital identity in a cost-effective and efficient way, then ProServeIT’s Alarm Guardian could be the security solution that you are looking for. Learn more about Alarm Guardian here, then contact us to get started today!
Content from: Cybersecurity Framework Webinar Series by George Abou-Samra
Edited by: Rachel Nguyen and Betty Quon
Tags:
May 17, 2022
Comments