What Is IT Security & Why It Matters More Than Ever
In a rapidly evolving work landscape, flexibility is critical. Surprisingly, 87% of employees offered flexible work options are making the most of them, working remotely for at least three days each week. However, this newfound flexibility comes with its own set of challenges. Recent statistics show that 68% of organizations have experienced one or more endpoint attacks that compromised their data and IT infrastructure. Additionally, 72% of organizations have reported increased complexity within their IT environment over the past two years.
What is Microsoft Intune, and how can it help your organization? Are you looking to streamline your workflow and empower your IT team to do more with less while enhancing device security? Look no further. In this blog, we’ll take you on a journey to unlock the power of Microsoft Intune. This game-changing cloud-based endpoint management solution transforms how organizations manage their devices, secure their data, and simplify app and device management.
In this blog, you will find:
🛠️ What Are Microsoft Intune's Core Capabilities?
✨ What Are Microsoft Intune Features and Benefits?
🔧 Microsoft Intune Solves 6 Common Business Problems
🚀 How to Deploy and Configure Microsoft Intune
🔗 How Microsoft Intune Integrates with Other Applications?
🏥 Milton Keynes University Hospital Secured Their End-Points with Microsoft Intune
Read along to discover what Microsoft Intune is and the six common business problems it helps solve. Plus, explore some key Microsoft Intune features and benefits.
What Is Microsoft Intune?
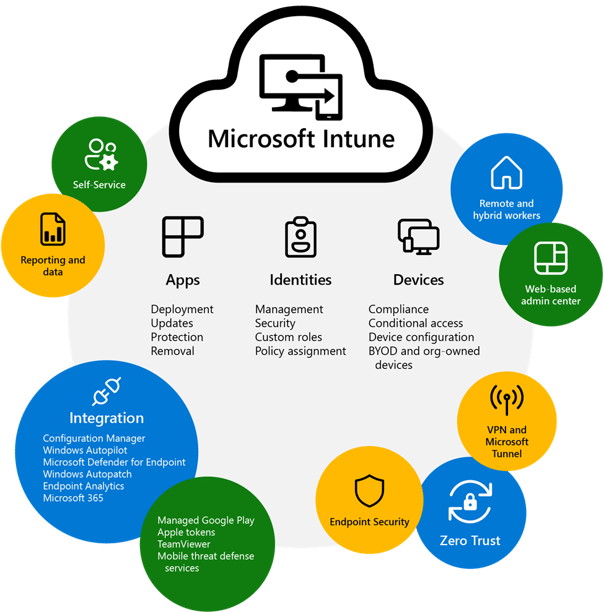
Microsoft Intune is a cloud-based enterprise mobility management (EMM) solution by Microsoft 365 that can help you manage the mobile devices and apps that your company-owned devices and employees use to access your corporate data. With Intune, you can ensure that any devices and apps your employees are using comply with your company’s security requirements. One essential feature of Intune is the Intune portal, a centralized platform where IT administrators can manage and monitor devices, deploy policies, and configure settings.
The Microsoft Intune Suite offers comprehensive features such as managing users and devices, simplifying app management, automating policy deployment, using self-service features, integrating with mobile threat defense, utilizing a web-based admin center, advanced endpoint management and security, and using Microsoft Copilot in Intune for AI-generated analysis.
Intune’s integration with other Microsoft Services like Microsoft Entra ID and Microsoft Defender for Endpoint creates an overall comprehensive system of managing various platforms such as on-premises, cloud, mobile desktop, or virtual endpoints across different operating systems ranging from Windows to Linux. Its advanced endpoint features also enable organizations to efficiently secure user access while upholding data protection rules within their own set parameters. This is very helpful when seeking compliance and is attainable with the configuration of user access policies, including those associated with smartphones and tablets running on iOS or Android!
An essential part of Microsoft Enterprise Mobility + Security, Microsoft Intune helps you manage your mobile environment. By providing device and mobile application management, Intune helps you give your users secure access to their data so they can stay productive while keeping that corporate data protected at all times.
Cloud-based Endpoint Management
Organizations looking to manage and protect their mobile devices have a great solution with Intune’s cloud-based unified endpoint management. This solution allows central control of the endpoints, from software deployment to security policies, and devices can be monitored through an easy web console for configuration. This approach is advantageous due to the scalability of cloud computing remote monitoring capabilities, eliminating the need for onsite servers and increasing protection and productivity gains. With real-time visibility into device activities, organizations gain immense flexibility while ensuring that they adhere to compliance protocols.
Integration with Microsoft Services
When combined with Microsoft Entra ID and Microsoft 365 services, Microsoft Intune provides a complete management experience. By integrating these features, it can ensure that only authorized personnel have access to company resources. Windows Autopilot also works seamlessly with Intune, delivering brand-new devices from device suppliers into users' hands faster.
Furthermore, integrating Microsoft Defender for Endpoint within Intune grants improved security measures. These include threat protection, setting up policies that analyze files to look for potential dangers while reporting risk levels, and allowing organizations to maintain compliant environments through endpoint security provided by Defender endpoint toolsets on host systems.
What Are Microsoft Intune's Core Capabilities?
Microsoft Intune is a powerful tool allowing organizations to manage their devices and applications securely. Its main capabilities include mobile device management (MDM), which lets you oversee your hardware, and mobile application management (MAM) for extra protection of sensitive data. The platform provides zero-trust security measures so companies can comply with industry regulations. It offers support across various operating systems such as Android Open-Source Project (AOSP), iOS/iPadOS, Linux Ubuntu Desktop, macOS, and Windows client devices - making it an ideal solution to meet varied needs in today’s ever-changing tech environment. Organizations can efficiently control their equipment by providing this flexibility while protecting all involved parties from risk or harm.
Microsoft Intune is a powerful tool allowing organizations to manage their devices and applications securely. Its main features include Mobile Device Management (MDM), which lets you oversee your hardware, and Mobile Application Management (MAM) for extra protection of sensitive data. The platform provides zero-trust security measures so companies can comply with industry regulations. It offers support across various operating systems such as Android Open-Source Project (AOSP), iOS/iPadOS, Linux Ubuntu Desktop, macOS, and Windows client devices - making it an ideal solution to meet varied needs in today’s ever-changing tech environment. Organizations can efficiently control their equipment by providing this flexibility while protecting all involved parties from risk or harm.
Mobile Device Management (MDM)
Organizations can efficiently manage and secure corporate-owned and personal devices through Mobile Device Management (MDM) with Intune. Its comprehensive MDM capabilities allow administrators to remotely manage device management, maintain compliance across the board, and deploy apps. Employees or students who need support for their mobile needs are provided with a self-service portal called the Company Portal app that they can use to reset their PIN/password, install applications, join groups, etc. To ensure the security of data across platforms and keep threats at bay in this changing world, it provides advanced threat defense services when managing these various kinds of devices using its complete solution offerings.
Mobile Application Management (MAM)
Mobile Application Management (MAM) is a vital component of Intune, used by organizations to gain control over mobile applications utilized by personnel and guarantee corporate data security through app protection policies. Enterprises can assign apps to employees and configure them with standard settings while keeping their sensitive information safe. MAM features such as license management, distribution, provisioning and configuration profiles for unenrolled devices let enterprises achieve an ideal balance between productivity and safety when using Intune’s solutions. Organizations thus have access to all the tools they need without jeopardizing enterprise-level security measures in any way, shape or form. Intune's app protection policies can also safeguard applications like Microsoft Teams on personal devices in a hybrid work environment.
Zero Trust Security Model
Intune’s zero-trust security framework is a cutting-edge tool for organizations striving to improve their cybersecurity measures. This model assumes that all users, applications and devices are untrustworthy until they are properly authenticated and approved to access resources. Applying this security concept dramatically lessens the threat of data breaches or unauthorized exposure to confidential information experienced by companies.
The setup encompasses user authentication processes, device compliance strategies, and network connection protocols. Also included are multi-factor identity verification methods, adherence policies for equipment requiring safety regulations, and segmentation approaches limiting sensitive information access. By embracing these principles, employers can acquire advanced protection against data threats while gaining visibility into any related activity conducted by users or devices.
Microsoft Intune Features & Benefits
Here are some of the features and benefits of using Microsoft Intune in your organization:
Features:
✅ Manage users and devices, including both organization-owned and personal devices.
✅ Supports Android, Android Open Source Project (AOSP), iOS/iPadOS, macOS, and Windows client devices.
✅ Simplifies app management with built-in app experience, including app deployment, updates, and removal.
✅ Automates policy deployment for apps, security, device configuration, compliance, conditional access, and more.
✅Offers self-service features in the Company Portal app for employees and students.
✅Integrates with mobile threat defense services, including Microsoft Defender for Endpoint and third-party partner services.
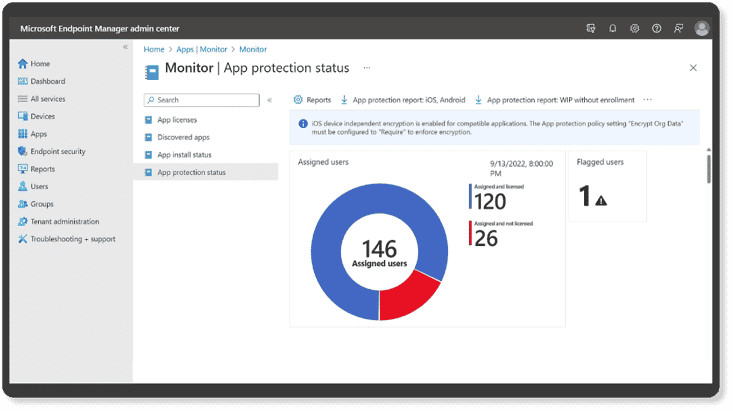
✅Uses a web-based admin center that focuses on endpoint management, including data-driven reporting
Benefits:
☑️ Microsoft Intune helps you keep your employees secure while staying productive.
☑️ Through Office 365 mobile app management, you can set policies to control access to your corporate data.
☑️ Microsoft Intune provides flexibility and control for securing your data, regardless of the device.
☑️ Microsoft Intune secures Android, iOS, Windows, and macOS devices with one unified mobile solution.
 Register Now for our On-demand Cybersecurity webinar on Microsoft Intune: Revolutionize Your Company's Device Management with Microsoft Intune.
Register Now for our On-demand Cybersecurity webinar on Microsoft Intune: Revolutionize Your Company's Device Management with Microsoft Intune.
Microsoft Intune Solves 6 Common Business Problems
Here are the top 6 common business problems that Microsoft Intune helps solve for organizations:
1. Intune solves the problem of your employees being able to access on-premise email and data securely.
Many organizations still have on-premises servers (i.e., Microsoft Exchange), but their employees must access their email and data securely. Using Intune-managed certificates combined with a standard VPN gateway or proxy (like Microsoft Entra application proxy documentation), you can enable access to mobile apps that connect to on-premises data. Once your employees’ devices are enrolled in Intune, the full endpoint management and system will help ensure they comply with your policies before accessing your corporate data.
2. Intune solves the problem of ensuring secure access to email and data through Microsoft 365.
Through Intune and Microsoft Enterprise Mobility + Security (EM+S), your organization can take advantage of a conditional access solution, which ensures that none of your employees’ apps or devices can access your Office 365 data unless they are in compliance with your company’s requirements that you’ve put into place.
For example, if you require multi-factor authentication for your employees to access your corporate data, Intune and Microsoft EM+S will not allow them to do so until they have met the MFA criteria. You can also require that your employees be enrolled with Intune before corporate data can be accessed.
3. Intune can help issue corporate-owned phones to your workforce.
Your employees need access to corporate apps and data that help them do their jobs anytime, wherever they are. However, you must ensure that your corporate data is secure and that your administrative costs are kept low.
With Intune, you can get bulk provisioning and management solutions, which are integrated with device management platforms (like the Apple Device Enrollment Program or the Samsung Knox mobile security platform). How does this help you? You can give an employee an unopened iPhone or Samsung device, and all they have to do is power it on, then get walked through a corporate-branded setup to authenticate themselves. That device is configured with security policies and the employee can launch the Intune Company Portal app that helps them access the apps you’ve made available to them.
4. Don't want to use corporate devices? Intune helps you secure Bring-Your-Own-Device (BYOD) programs for your employees.
Many employees don’t want to carry a second device around, so Bring-Your-Own-Device (BYOD) programs are growing in popularity among organizations. However, getting employees to enroll their devices into a management program is a major challenge because many employees don’t want their employers to have access to their devices.
Intune offers a BYOD approach that employees can get on board with. It manages only the apps containing corporate data (like Microsoft mobile apps), which protects your corporate data even if the app in question pulls from corporate and personal data sources. Also, you can implement protection policies that prevent your employees from copying text from a corporate email profile into a consumer email profile, even if run within the same Outlook mobile app.
5. Intune lets you issue limited-use shared tablets with your employees.
There are several instances where employees need to have a device, like a tablet, to do their jobs. For instance, you may have noticed several retail employees carrying tablets around to check inventory, process a sale, or assist a customer. These tablets are usually in limited-use mode, allowing employees to access only the app(s) needed to do their job.
Like the corporate-owned phones we discussed earlier, Intune lets you bulk provision, secure, and manage iOS and Android tablets to run in a limited-use mode that will be shared among your employees.
Related blog:
✈️ How to Boost Your Endpoint & Device Management with Microsoft Intune
💻 Unlock the Power of Microsoft 365 for Seamless Hybrid Work
6. With Intune, you can limit employee access to corporate data only to your control devices.
Have your employees ever used a public kiosk to access their corporate data (for instance, used a public computer at a trade show or in a hotel lobby to sign into their email)?
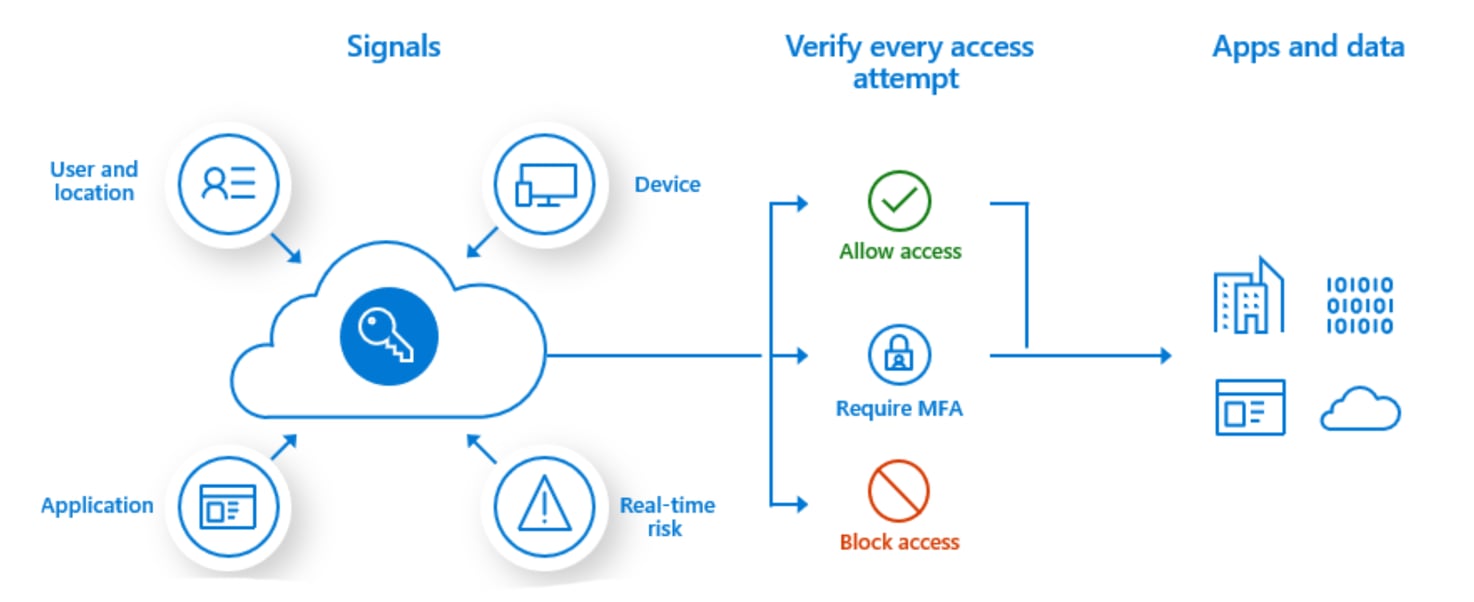
Microsoft Intune and Microsoft Enterprise Mobility + Security lets you limit the access to your corporate data to only devices that your organization manages. With Intune, you can give conditional access to your employees based on if the device is corporate-owned if it’s part of a BYOD program that your organization allows or other criteria. Intune also allows for app-based conditional access as well.
Ready to streamline your IT management with Microsoft Intune?
How to Deploy and Configure Microsoft Intune
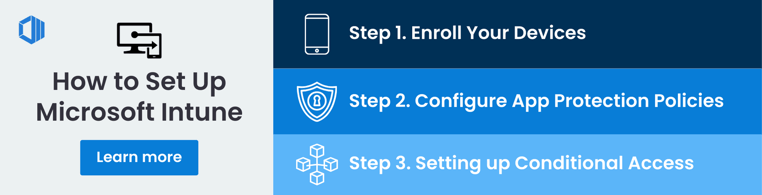
Organizations can ensure effective deployment and configuration of Microsoft Intune to maximize device management, security protocol enforcement and compliance assurance. A structured process should be followed, consisting of enrolling devices, setting up app protection policies, and configuring conditional access rules.
The guides provided by the Intune documentation can offer additional support for successful set-up while allowing IT administrators to effectively manage their organization's applications data alongside all related devices.
Step 1. Enrolling Devices
Enrolling devices into Intune is essential to deployment, enabling organizations to manage and protect their corporate data. It involves connecting and configuring each device with a management platform or system, allowing administrators to access them remotely.
Having managed devices enrolled in Intune can be monitored continuously and kept secure through company policies while providing control for application delivery. This approach secures sensitive information across multiple platforms effectively.
Step 2. Configuring App Protection Policies
Creating app protection policies is critical to the Intune deployment process to ensure corporate data security. These rules and policies provide an essential balance between allowing employees necessary productivity tools while restricting sensitive information in managed apps. This helps businesses comply with industry regulations by protecting confidential data from unauthorized access or misuse.
Step 3. Setting up Conditional Access
Organizations can leverage conditional access rules to ensure more secure and controlled access for users who wish to utilize cloud apps or other resources. It can be achieved by allowing administrators to monitor the activity at both the user and device level, enforcing measures such as multi-factor authentication (MFA) or evaluating compliance before granting permission.
By configuring these policies, IT teams can boost security and gain increased visibility into the authorization process, guaranteeing that only authorized parties can access company information through various tools and services.
Price of Microsoft Intune and Microsoft Intune Suite
Intune is offered monthly per user, allowing organizations to acquire it as a standalone or bundled subscription. There are three distinct plans available for purchase:
✅ Microsoft Intune Plan 1 provides essential UEM functionality and is bundled with Microsoft 365 E3, E5, F1, F3, EMS E3 & E5, and Business Premium subscriptions. Additional tools from the Microsoft Intune Suite can be incorporated into Plan 1, offering a comprehensive solution. The pricing stands at $8 per user per month.
✅ Microsoft Intune Plan 2 is a valuable extension to Plan 1, providing additional features such as Microsoft Intune Tunnel for Mobile Application Management (MAM) and specialized endpoint management capabilities. The subscription cost for Plan 2 is $4 per user per month, in addition to the $8 fee for Plan 1.
✅ The Microsoft Intune Suite is a premium standalone service with features from Plan 2 and advanced tools like Remote Help, Endpoint Management, and endpoint analytics. Priced at $10 per user per month, it complements the $8 cost of Plan 1 to provide a comprehensive solution for organizations.
How Microsoft Intune Integrates with Other Applications?
Microsoft Intune bolsters its features with integrations from third-party services like Managed Google Play, Apple Certificates and TeamViewer to increase effectiveness in the deployment of apps, improve device management capabilities, and allow remote user support. All these tools combine to give a more robust set of functionalities for enhanced device control.
Managed Google Play and Apple Certificates
Integration with Managed Google Play and Apple certificates allows streamlined app deployment on mobile devices. Connecting to the organization's private store for Android apps enables administrators to deploy these applications across platforms quickly and securely. Integrating Apple tokens/certificates into Microsoft Intune also permits iOS, iPadOS, and macOS devices to enroll in Intune policies and access volume-purchased licenses for compatible apps for installation onto their respective mobiles.
By incorporating both integrations, companies gain a more efficient approach when managing applications across multiple device environments simultaneously.
Remote Assistance with TeamViewer
TeamViewer is an efficient and widely accepted tool for providing help remotely, allowing IT professionals to easily access any device on the network and give assistance even if they are not in person. With Microsoft Intune incorporating TeamViewer alongside its Tunnel feature, organizations have a powerful combination that can quickly identify issues with enrolled devices while preserving user productivity. Intune's flexibility provides enhanced capabilities allowing companies to address their unique requirements confidently.
Milton Keynes University Hospital Secured Their End-Points with Microsoft Intune
Milton Keynes University Hospital (MKUH) is strategically located between London and Birmingham, offering innovative health services and technology-driven patient care within the United Kingdom's National Health Service (NHS).
To ensure the confidentiality and security of crucial patient data necessary for adequate care, the hospital has implemented Microsoft Intune. This cloud-based endpoint management solution equips MKUH with a robust set of modern cloud security and application management tools for all endpoints, including on-premises, cloud, and virtual, across various devices, operating systems, and platforms.
With the implementation of Intune, the hospital's IT team can now cater to the diverse requirements of frontline workers, providing them with secure and efficient access to specialized devices and applications tailored for the clinical setting. Furthermore, the team can streamline the management and security of a more comprehensive array of iOS and Android devices, ensuring the hospital staff has the tools to deliver optimal patient care and experiences.
Conclusion
Microsoft Intune emerges as a powerful cloud-based management solution, offering a range of features, from mobile device and application management to a robust zero-trust security model. With these capabilities, organizations can efficiently manage devices, all while ensuring compliance with regulations, empowering employees, and driving productivity.
Microsoft Intune doesn't stop at device management; it simplifies cybersecurity by unifying monitoring and reducing complexity. This streamlined approach minimizes the need for multiple cybersecurity platforms, reducing IT management burdens and costs. Contact us today for more insights into how Microsoft Intune can strengthen your hybrid workforce's security and streamline IT management. Your path to enhanced efficiency and security starts here.
Tags:
.webp?width=120&height=120&name=Hyun%20Blog%20(1).webp)
July 09, 2024
.png?width=762&height=195&name=Intune-case-study-banner%20(1).png)
.png?width=500&height=500&name=cyber%20security_110110543%20%5BConverted%5D%20(3).png)



Comments