As the digital world continues to expand and evolve, so does the need for robust cybersecurity solutions. In today's connected landscape, organizations must protect their networks from a variety of threats by utilizing effective endpoint security and management practices. Microsoft Intune is an essential suite of tools that can help increase IT efficiency while also providing increased protection against cyberattacks on Internet of Things (IoT) devices and Operational Technology (OT).
This article will discuss insights into the Endpoint Vulnerability Gap in Mid-Market & Enterprise Organizations (North America) and how Microsoft InTune can help with your endpoint management needs. We'll also be exploring the Microsoft 365 E3 Do More with Less (DMWL) promotional offer, which offers businesses an easy way to get started with these robust cybersecurity solutions.
In a hurry? Jump straight to your section of interest:
Unveiling The Cybersecurity Trends for Internet of Things (IoT) and Operational Technology (OT)
Increase IT Efficiency and Cybersecurity with Microsoft Intune Suite
How Can Microsoft InTune Help with Your Endpoint Management?
Microsoft 365 E3 Do More with Less (DMWL) Promotional Offer
Learn More about Cybersecurity for Your Organization in 2023
Unveiling The Cybersecurity Trends for the Internet of Things (IoT) and Operational Technology (OT)
The Internet of Things (IoT) and Operational Technology (OT) are two emerging technologies that have the potential to revolutionize the way businesses operate across the globe.
The Internet of Things (IoT) represents a network of interconnected devices that can collect and share data, allowing for more efficient processes such as predictive maintenance and asset management for facility management operations. It can also provide insight into customer behavior which can be used to target marketing efforts better or to identify new revenue streams. Operational Technology (OT) is a combination of hardware, software, and digital connectivity designed to help organizations automate their operations and improve productivity. This includes applications such as robotics, process digitization, automated inspections, and more.
Utilizing both IoT and OT can provide organizations with numerous benefits, such as improved operational efficiency, reduced costs, improved safety protocols, and greater customer service capabilities. Furthermore, it can help companies prepare for disruptions in the marketplace by providing them with real-time insights into their operations, leading to faster decision-making processes.
While businesses have much to gain from investing in IoT and OT technologies, their rapid adoption across many local, national, and international organizations now represents a sizable opportunity for cybercriminals or threat actors to digitally attack any business with weak (or non-existent) cybersecurity defenses.
IoT devices—including monitoring systems, HVAC devices, and building access controls— can represent exceptional cybersecurity risks to networks, individuals, and organizations. The swift implementation of IoT solutions in many industries globally has led to an increase in organizational exposure risk as well as the number of possible attack vectors. The risk exposure doesn’t just rest with the organization in question. If any of their third-party vendors are compromised via a cyberattack, this could give hackers access to the networks that those vendors are connected to.
Below is a summary of the main types of cyberattacks on IoT/OT.
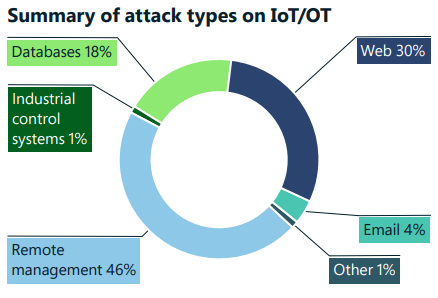
Source: Microsoft Digital Defense Report 2022
As shown in the chart above, the top 3 attacks on IoT/OT are remote management (46%), web (30%), and databases (18%). IoT devices pose unique security risks as entry and pivot points in an organization’s network. Despite this threat, millions of IoT devices are exposed or have no security patch program.
Threat actors can utilize such exposure to devastating effect, as evidenced by the steady increase in cyberattacks on remote management devices between 2021 and 2022 (see graph below).
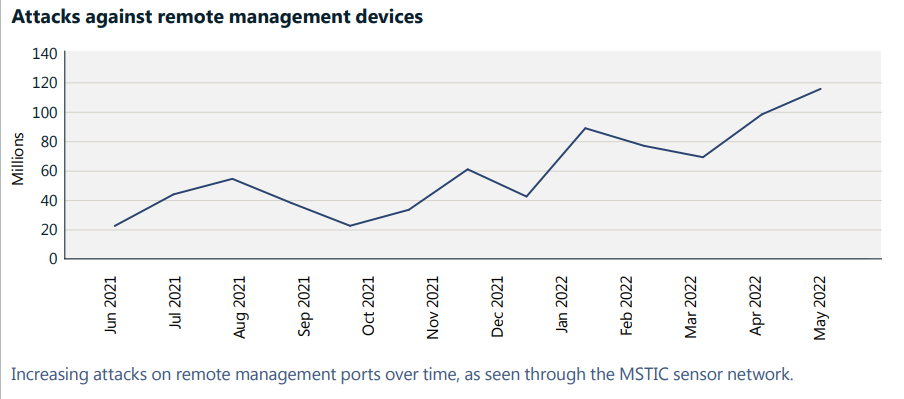 Source: Microsoft Digital Defense Report 2022
Source: Microsoft Digital Defense Report 2022
Open network ports are generally used for the remote management of devices.
According to Microsoft’s cybersecurity research last year, cybercriminals can discover vulnerable organizational devices through online tools that detect services that are “listening” on open network ports. The ability to “listen” in on an open network port can help a hacker gauge if the connected device can be used as a “pivot point” to infiltrate yet another layer of an organization’s network (especially if there is no cyber threat detection system in place).
What can be done to protect the IoT/OT in your organization?
Here are a few suggestions from Microsoft’s Security Team:
Make certain industrial control system (ICS) protocols are not exposed directly to the internet.Ensure devices are robust by applying patches, changing default passwords, and default secure shell (SSH) ports.
Use an IoT/OT-aware network detection and response (NDR) solution and a security information and event management (SIEM)/security orchestration and response (SOAR) solution to monitor devices for anomalous or unauthorized behaviours, such as communication with unfamiliar hosts.
How to Increase IT Efficiency and Cybersecurity with the Microsoft Intune Suite
Insights on the Endpoint Vulnerability Gap in Mid-Market & Enterprise Organizations (North America)
In 2022, TechTarget’s Enterprise Strategy Group (ESG) surveyed 381 IT and cybersecurity decision makers in North America involved with security technologies and endpoint management at mid-market (100 - 999 employees) and enterprise (1,000+ employees) organizations.
The results highlighted a sizable discrepancy in how organizations address their endpoint security concerns as part of their broader cybersecurity strategy. According to their findings, “80% of organizations are actively monitoring at least half of their devices, only 10% do so for all of their endpoints” (see infographic below).
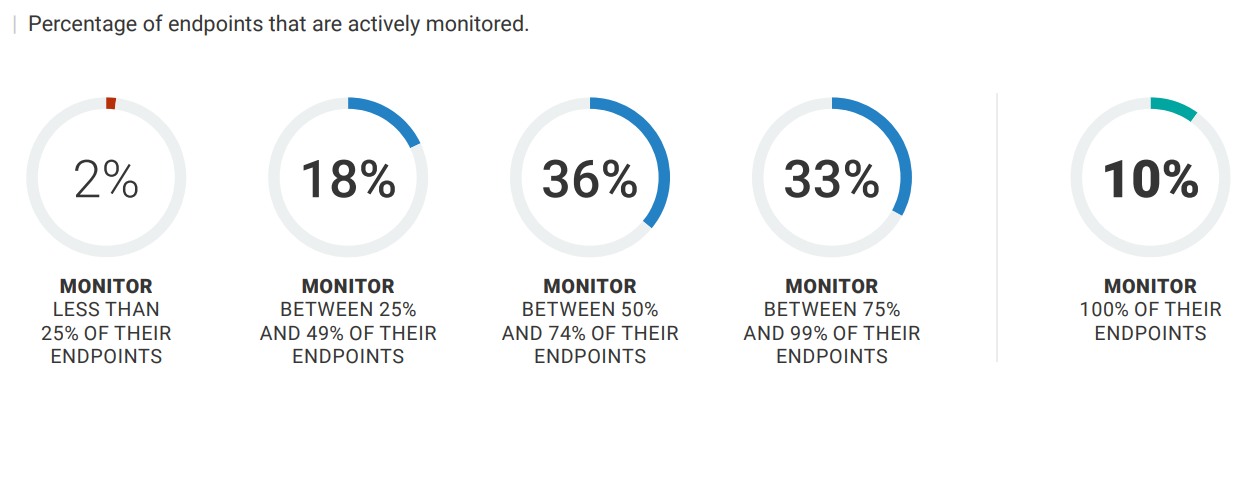 Source: Enterprise Strategy Group by TechTarget
Source: Enterprise Strategy Group by TechTarget
That lack of vigilance (only 10% of the respondents for the study were monitoring all their endpoints) highlights a critical gap in the cybersecurity stance of several companies, especially those that view device management as yielding the same level of cybersecurity as endpoint monitoring. Therefore, it is no surprise that of the surveyed organizations, more than 70% experienced cyberattacks caused by an unknown, unmanaged, or poorly managed endpoint. Of that number, 34% experienced several cyberattacks, while 43% experienced only a single cyberattack.
The final insight to highlight from this study is that “those organizations exceeding the 20% threshold in terms of unmanaged devices are nearly 11x likelier than those with less than 5% unmanaged devices to have experienced several endpoint-focused cyberattacks”.
How can your organization address its Endpoint Vulnerability Gap in 2023? Read below to learn more.
How Can Microsoft InTune Help with Your Endpoint Management?
Microsoft Intune is an industry-leading, unified endpoint management solution that companies utilize to ensure their operating systems, devices, and business applications are secured and updated (especially when it comes to the evolving landscape of cyber threats and ransomware).
This unique solution can help your organization to:
1. Strengthen its cybersecurity. Mitigate threats to devices, protect corporate data, and improve compliance with advanced security features.
2. Reduce IT costs. Do more with less by consolidating your endpoint management and security vendors and optimizing performance across devices.
3. Unify your endpoint management. Simplify IT and security workloads by combining your endpoint and security management tools.
According to recent Microsoft data, 57% of organizations do not have visibility or control over a quarter of their endpoints or more. A comprehensive endpoint security solution like Microsoft InTune allows you to take advantage of the full picture of your endpoint management, giving superior visibility into potential threats and vulnerabilities. With unified data sources in a single dataset, there are fewer blind spots - meaning more actionable insights for your organization’s improved cybersecurity.
“The Microsoft Intune Suite is going to help us consolidate our endpoint management solutions, saving costs, making our lives easier, and keeping the hospital data secure. I would highly recommend the Microsoft Intune Suite to any organization looking to enhance their security posture.” - Ibrar Mahmood (IT Cyber Security Manager - Milton Keynes University Hospital NHS Foundation Trust)
Microsoft InTune can help simplify your cybersecurity and reduce “mental overhead” (due to work aligning multiple cybersecurity monitoring platforms). This is done by creating a unified admin console with all required workflows instead of using different admin consoles to monitor different parts of your IT environment.
Interested in learning more about this solution as well as how you can secure your hybrid workforce, reduce IT management and complexity, and cut IT costs? Register for our Cybersecurity Bonus Webinar: Revolutionize Your Company's Device Management with Microsoft Intune today!
Microsoft 365 E3 Do More with Less (DMWL) Promotional Offer
Microsoft is thrilled to announce a new promotional offer for Microsoft 365 E3 under the Do More with Less (DMWL) campaign.
The Microsoft 365 E3 solution blends critical quality applications to help increase work productivity and collaboration while helping to secure your organizational data with intelligent security. Below is a list of some of the business applications available with this solution.
 For a limited time, customers new to Microsoft 365 E3 can enjoy an exclusive 15% discount on the net partner price! This is for customers who haven’t previously purchased Microsoft 365 E3 on any platform (legacy or new commerce) or channel (direct, CSP, or Enterprise Agreement). Customers are subject to the first purchase constraint. For more information about customer eligibility criteria, see New commerce promotions.
For a limited time, customers new to Microsoft 365 E3 can enjoy an exclusive 15% discount on the net partner price! This is for customers who haven’t previously purchased Microsoft 365 E3 on any platform (legacy or new commerce) or channel (direct, CSP, or Enterprise Agreement). Customers are subject to the first purchase constraint. For more information about customer eligibility criteria, see New commerce promotions.
This offer is valid from February 1, 2023, to June 30, 2023. Upon the annual subscription’s renewal date, standard pricing will apply.
For organizations who choose to commit to an annual subscription to Microsoft 365 E3, promotional pricing will apply through the entire subscription term—yet another exciting reason to move to Microsoft 365 E3.
Interested in moving your business into the future with Microsoft 365 E3 today? Talk with one of our experts to see how we can get you started!

Learn More about Cybersecurity for Your Organization in 2023
Not sure what steps you need to take to improve your organization’s cybersecurity stance? Check out our free course on Cybersecurity brought to you by our new ProServeIT Academy.
This course has two informative classes, delivered online by our in-house Cybersecurity expert, and is designed for IT leaders and professionals. See our list of classes below:
👤 Class 01: Protect Against Phishing Scams and Identity Theft
Are you tired of falling victim to phishing scams and identity theft? Protect yourself and your personal information with our comprehensive guide on identifying and avoiding these malicious attacks.
Our experts will share the latest tactics used by cybercriminals and real customer stories and provide you with practical tools and strategies to safeguard yourself and your personal information with data protection solutions and data breach prevention best practices.
Join us for a live, interactive session to learn easy steps you can take to safeguard yourself online. Don't become a statistic – stay informed and protected with our expert advice! Take control and learn from the best to cyber-protect yourself online.
Course Delivered: Online
Click here to register for this class.
🤖 Class 02: The Good and Bad of AI in Cybersecurity
Are you curious about the potential of Artificial Intelligence (AI) in cybersecurity but also concerned about the potential risks?
Join us for an enlightening session where we'll dive deep into the good and bad of AI in cybersecurity. From its ability to quickly detect and respond to cyber threats to its potential for misuse, this class will provide you with a comprehensive understanding of the impact of AI on cybersecurity. We’ll share a real-life scenario to illustrate what can happen.
Whether you're a business owner, IT professional, or just someone who wants to stay informed, you won't want to miss out on this opportunity to learn from experts in the field. So, mark your calendar, and get ready to explore the exciting and ever-evolving world of AI in cybersecurity.
Course Delivered: Online
Click here to register for this class.
Conclusion
From insights regarding Endpoint Vulnerability to understanding how Microsoft InTune can help with endpoint management, it's clear that modern businesses need robust cybersecurity solutions. With tools like Microsoft Intune, organizations have access to a suite of powerful and effective security solutions to help better protect endpoints including their IoT devices and Operational Technology (OT).
Does your organization know about its endpoint vulnerability gap? Do you need help addressing this critical issue? We'd be happy to talk with you and see if Microsoft InTune is the right tool for your organization.
Tags:

November 22, 2023

Comments