What Is IT Security & Why It Matters More Than Ever
Summary
As businesses add more vendors, complexity grows—bringing security gaps, inefficiencies, and higher costs. This blog explains why vendor risk is a critical issue for today’s leaders and offers five practical tips to reduce exposure, including asking the right security questions, running “what if” scenarios, and creating scalable contingency plans.
You’ll also learn how consolidating your IT vendor model with a strategic partner can simplify operations, improve accountability, and enhance cybersecurity. Real-world examples like the Target HVAC breach and Sunwing outage show why proactive vendor risk management matters now more than ever.
Managing vendor risk is essential, but if you’re like most business leaders today, the bigger challenge is managing the growing number of vendors in your IT environment. More vendors often mean more tools, more complexity, and more gaps in accountability. This complexity leads to security vulnerabilities, inefficiencies, and higher costs, particularly when no single partner oversees the entire IT strategy. That’s why vendor risk management must go hand-in-hand with vendor model management.
Let’s explore how you can better manage both, and how a strategic IT partner can make it simpler.
Table of Contents
⚠️ Understanding the Risks: Why Focusing on Tech Vendor Risk Matters
✋ Five Tips for Mitigating Organizational Tech Vendor Risk
Tip #1: Ask the Right Questions About Tech Vendor Security
Tip #2: Run “What If” Scenarios to Spot Weak Links
Tip #3: Evaluate Where You Can Reduce Risk Now
Tip #4: Create a Simple, Scalable Contingency Plan
Tip #5: Simplify Your Tech Vendor Model with a Strategic Partner
⏭️ Why This Matters for Today’s Leaders
🗣️ A Final Word: You Don’t Have to Manage It All Alone
Understanding the Risks: Why Focusing on Vendor Risk Matters
One of the most significant elements of risk that a company has (from a security perspective) is its third-party vendors, and this risk element is often outside of its control. There are various forms of risk. When discussing security risks, an organization can be in control by using different security tools and technologies to help secure its technology environment.
Despite this level of control, users can represent the weakest link in an existing cybersecurity system. If a hacker gets access to an employee’s password, that employee’s access can now become a proxy for said "hacker" to attack your organization. Similarly, your partners or vendors (depending on their critical role in your business) could also represent a significant component of your risk.
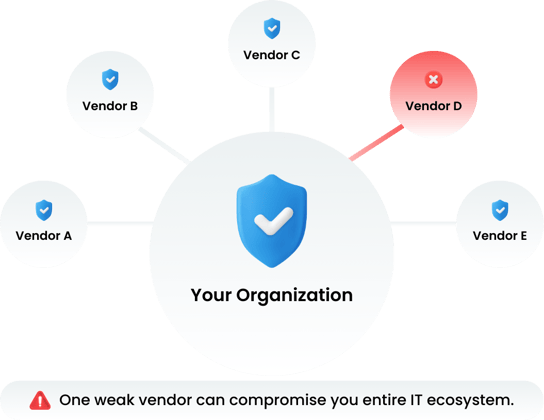
Vendor risk is a significant issue for organizations, as the potential risks associated with vendor relationships go far beyond financial concerns. Without proper vendor risk management, organizations are exposed to various threats that could damage operations and trustworthiness in customers' eyes. Potentially more significant damage can result when your vendor partner’s poor performance affects your organization due to interdependent services or resources.
Organizations must ensure vendor protection by performing thorough vendor risk assessments before engagement and having procedures in place for ongoing management. This process enables the organization to gain insight into vendor activities and relevant policies, mitigating vendor-related risks and ensuring compliance with data protection laws such as GDPR or HIPAA1.
The Risk of Vendor Services: How a Heating, Ventilation, and Air Conditioning (HVAC) Company Impacted Target's Cybersecurity (A Vendor Risk Story)
This is an example of how vendor risk can impact an organization using something as innocuous as a heating, ventilation, and air conditioning (HVAC) company.
In 2013, Target, a major U.S. retailer, used an HVAC company2 to service the ventilation in their buildings. The problem Target encountered was that the HVAC company was compromised by hackers who stole network credentials that allowed them to get into Target’s proprietary network.

It was an unforeseen situation. How could an HVAC company servicing Target's buildings be a risk from a cybersecurity perspective? Well, it was for Target, and it caused severe financial repercussions; the breach exposed 40 million debit and credit card accounts.
A fraud analyst for Gartner Inc. estimated that "Target could face losses of up to $420 million due to the breach". An expensive price tag for any organization.
5 Tips for Mitigating Organizational Vendor Risk In 2026
![]()
Tip #1: Ask the Right Questions About Vendor Security
Before bringing in any vendor, ask the tough questions:
- What are their internal cybersecurity protocols?
- Do they meet your compliance requirements (e.g., HIPAA, GDPR, ISO)?
- How do they manage sensitive data and access control?
If these questions aren’t being asked during onboarding, your business could be exposed. A proactive vendor risk assessment ensures you know what you're dealing with before it's too late.
🧠 Related reading: Define Risk Tolerance to Determine Your Security Strategy
![]()
Tip #2: Run “What If” Scenarios to Spot Weak Links 🤷♂️
What would happen if one of your key vendors was breached tomorrow? Would you be ready?
🤔 Consider:
- Which vendors are essential to your daily operations?
- What systems do they touch, directly or indirectly and what risks do they pose to your organization?
- What are the top 3 “what if” scenarios your organization should be prepared for?
- How would a failure impact your customers, revenue, or reputation?
Let’s look at another real-world example:
Sunwing’s 2022 system outage stemmed from a third-party ticketing provider3. Here’s what happened…
In April 2022, Sunwing had its ticketing system managed by a third-party vendor, and that vendor was hacked. This caused several problems for the airline:
❌ Bad public relations: negative brand perception due to news outlets publicizing that Sunwing was hacked. It was their ticketing vendor that was compromised, but the impact still hit Sunwing’s brand in a negative way.
❌ Additional work: due to the issue with their ticketing system vendor, Sunwing was forced to conduct their ticket booking manually.
❌ Cost: this incident cost Sunwing a significant amount (not just in the capital alone). They had to pay their team for overtime and compensate travelers for the issues with their bookings (and additional costs due to flight cancellations).
It is important to emphasize that Sunwing itself wasn't compromised in this situation. Still, the compromised party was a vendor that was providing the ticketing and boarding services to the airline company.
So not only can a supply chain attack have an immediate financial impact, but it can also have a trailing financial impact based on lost potential revenue from customers due to the negative news about the impacted company. This can also erode any trust between the company and its existing (and future) customers. It can take time and money to rebuild that trust as a business.
It is worth going through a “what if” thinking exercise for your organization. Better to do it now when you are calm than when a cyberattack occurs because, at that point, your brain might be in fight or flight mode (that moment) due to the severity of the situation. Suppose a breach occurs and your vendor is compromised. In that case, this might put your organization in pure reaction mode, where people are testing different solutions as opposed to implementing an existing cybersecurity emergency plan.
If an organization undertakes this type of strategic exercise, it can better manage a crisis in the future and reduce its related risk.
🛡️ Want to get ahead of risk? Check out our Cyber Attack Prevention Guide.
![]()
Tip #3: Evaluate Where You Can Reduce Risk Right Now
You don’t need a complete overhaul to improve your vendor risk posture. Start with low-hanging fruit:
- Reassess current vendor SLAs and contracts
- Add security clauses where needed
- Require vendors to share audit logs or breach notifications
For high-risk vendors, consider implementing redundancy or backup options, especially for services tied to data, payments, or infrastructure.
🤔 Key questions to consider when evaluating what changes can be made:
- Does your organization have a security protocol?
- Does your organization have contingencies in place related to existing vendor risk?
- What type of security initiatives does your organization have in place?
- How does your organization secure its data?
- What is your organization’s disaster recovery plan?
Need more support? Our Digital Transformation Consulting team helps businesses build resilient tech ecosystems.
![]()
Tip #4: Create a Simple, Scalable Contingency Plan
You don’t need to overcomplicate things. Even a basic plan can make a big difference in a crisis:
- Identify your business-critical vendors
- Clarify how to communicate in case of a breach
- Define your internal response team and who does what
Remember: when something goes wrong, your reaction speed and clarity of response are everything. It’s not just about preventing risk, it’s about preparing to respond confidently when it arises.
🤔 Key questions to consider when creating a basic contingency plan:
- What can be done proactively and intentionally to ensure your organization is as secure as possible?
- What steps have your business-critical vendors taken to ensure they are well-defended against supply chain attacks?
- How do you audit your vendors from an IT security perspective?
- What needs to be updated in your existing vendor selection process?
- Have your vendors updated their contingency plans regarding a cyberattack?
📘 Related Blogs:
- How to Evaluate Your Core Business Applications? | Risk Value Matrix
- Define Risk Tolerance Level to Determine Your Information Security Strategy
- How to Choose & Invest in the Right Technology Tools for Your Company?
![]()
Tip #5: Simplify Your Vendor Model with a Strategic Partner 🤝
Here’s the truth: managing risk becomes exponentially harder when you're juggling 10+ vendors across your IT stack.
Instead of playing vendor “whack-a-mole,” consider consolidating your IT needs with a single, strategic managed IT services provider.
Here’s what that looks like:
- Fewer points of contact mean faster resolution and clearer accountability
- One unified security strategy across all your systems and software
- Proactive risk management from a partner who knows your entire IT landscape
- Simplified vendor negotiations, billing, and ongoing support
This is what ProServeIT’s Managed IT Services are built for. We become your single point of contact for all things IT, so you’re not left coordinating multiple vendors or wondering where the gaps are.
📖 Read more: The Benefits of Using Managed IT Services
Why This Matters for Today’s Leaders
Vendor risk is no longer a niche IT issue; it’s a boardroom issue. As companies rely more on third-party services, leaders must take a strategic approach to risk and vendor management.
This is especially critical for modernizing mid-sized businesses, where stretched IT teams can’t afford to chase vendor issues or plug security holes across dozens of platforms.
📚 Planning your next transformation initiative? Read:
- Top Digital Transformation Challenges in 2026
- Why IT Strategy Matters: Aligning Technology with Business Goals
Take Control of Vendor Risk Today
Don’t wait for a breach to happen. Partner with ProServeIT to simplify your IT vendor model, strengthen security, and align technology with your business goals.
A Final Word: You Don’t Have to Manage It All Alone
Vendor risk management doesn’t have to fall entirely on your shoulders. As businesses grow, so does vendor complexity, bringing hidden risks, operational inefficiencies, and accountability gaps.
That’s where ProServeIT comes in. Our Managed IT Services don’t just help you manage vendor risk; we help you eliminate vendor chaos altogether. By consolidating your tech stack under one strategic partner, you gain visibility, reduce risk, and free up internal resources to focus on growth.
Let’s simplify your IT environment and build a smarter, more secure vendor strategy — together.
👀 Explore Our Managed IT Services
Sources:
1 Imprivata. “GDPR and HIPAA Compliance: What Are the Differences and How Can I Work Towards Compliance?” Imprivata, 25 May 2021, https://www.imprivata.com/blog/gdpr-and-hipaa-compliance-what-are-the-differences-and-how-can-i-work-towards-compliance.
2 Krebs, Brian. “Target Hackers Broke in via HVAC Company.” Krebs on Security, 5 Feb. 2014, https://krebsonsecurity.com/2014/02/target-hackers-broke-in-via-hvac-company.
3 PAX News. “Cyber-Attack behind Sunwing Outage; Carrier Working with Other Airlines as Delays Continue.” PAX News, 20 Apr. 2022, https://www.paxnews.com/news/tour-operator/cyber-attack-behind-sunwing-outage-carrier-working-other-airlines-delays-continue.
Tags:

November 12, 2025
.png?width=500&height=500&name=cyber%20security_110110543%20%5BConverted%5D%20(3).png)


Comments