What Is IT Security & Why It Matters More Than Ever
In a world increasingly connected by technology, the dark specter of ransomware attacks looms larger than ever before. Cybercriminals are relentlessly devising sophisticated attacks that can cripple businesses, institutions, and even governments. The need for a robust and proactive defense against these insidious threats has never been more crucial.
In this blog post, we will delve deep into the realm of ransomware attacks, dissecting the hard lessons learned from a recent encounter faced by Sysco, a leading player in the food service industry. We will explore Microsoft Security Copilot, a groundbreaking cybersecurity solution that seamlessly integrates the power of Artificial Intelligence (AI) to help organizations discover potential vulnerabilities, generate concise security reports, and swiftly respond to ongoing cyberattacks.
Join us as we unveil the potent synergy of AI and cybersecurity excellence. Learn more about the remarkable tale of Microsoft's Security Copilot (still under development) in the relentless battle against ransomware threats.
In a hurry? Jump straight to your section of interest:
🔦 Microsoft’s Spotlight on Ransomware Attacks
👤 Understanding Human-operated Ransomware Attacks
🛡️ Cybersecurity Strategy for Organizations
⚔️ Defense Strategies Against Ransomware
📝 Ransomware Attack Review: Lessons from Sysco
🤖 Microsoft Security Copilot: AI Meets Cybersecurity Excellence
Microsoft’s Spotlight on Ransomware Attacks
In 2022, Microsoft's ransomware experts carried out extensive investigations into over 100 ransomware incidents initiated by human operators. The objective was to monitor the attackers' methods closely and gain insights to enhance customer protection. Notably, this comprehensive analysis specifically targeted onboarded and managed devices.
Stages of Ransomware Attacks
A ransomware attack can occur in stages or phases, which allows attackers to infiltrate your organization and reach the valuable data within. While the stages may not occur in a linear sequence depending on the defenses encountered and other factors, here are the seven stages of a ransomware attack:
1. Reconnaissance 🔍
• Research and gathering of information about the target network or organization to identify vulnerabilities and potential entry points.
2. Weaponization 💳
• Creation of the actual ransomware payload or acquiring it from dark web sources.
• Combining the malicious code with exploit kits or other delivery methods.
3. Delivery 📧
• Sending the ransomware payload to the target system (i.e., your organization’s system), often through phishing emails, malicious attachments, or compromised websites.
4. Exploitation 🖱️
• Executing the ransomware payload on the victim's system to gain control and establish a foothold in the network.
5. Installation 🖥️
• Installing the ransomware payload and other tools to ensure persistence on the victim's system, even after reboots.
6. Encryption 🔐
• Scanning the victim's network for valuable files and encrypting them to render them inaccessible without the decryption key.
7. Extortion ⚠️
• Displaying the ransom note, demanding payment in cryptocurrency (to deter the payment from being traced) in exchange for the decryption key.
• Threatening to leak sensitive data if the ransom is not paid within a specified time frame.
An important point to highlight is that a ransomware attack might come as a surprise to the victimized party, but it is, in fact, a calculated attack on an organization by intelligent hackers. Such threat actors have gone through scoping out your organization’s digital weaknesses and strategizing how best to breach its defenses without being detected.
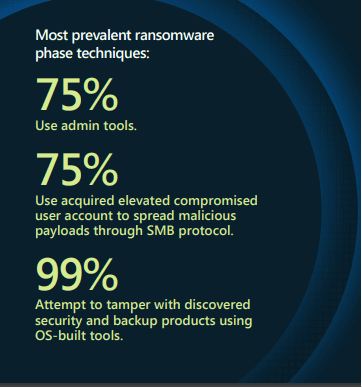
Image: Top 3 ransomware phase techniques used by hackers.
Understanding Human-operated Ransomware Attacks
Based on Microsoft's investigations, it was discovered that most threat actors orchestrating human-operated ransomware attacks exploit similar security vulnerabilities and employ shared attack patterns and techniques.
Human-operated ransomware attacks can be classified into two main phases: the pre-ransomware phase and the ransomware deployment phase (see infographic below).
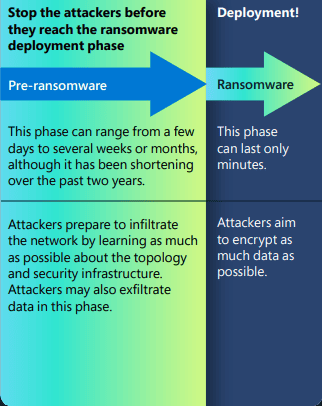
Image: The pre-ransomware phase and its link to the deployment of a ransomware payload.
Pre-Ransomware Phase
In the pre-ransomware phase, attackers diligently plan their intrusion into the network by studying the organization's structure and security infrastructure.
It is important to note the difference in length between the pre-ransomware phase and the actual deployment of the ransomware payload. As stated in the infographic above, the time spent in the pre-ransomware phase (Stage 1 of a ransomware attack – Reconnaissance) can vary from several days to months. During this phase, hackers are studying an organization’s system in preparation for a ransomware attack that will bypass any existing security infrastructure. In addition, they might also siphon any login information or credentials from personal/corporate devices, which will be used for the impending ransomware attack.
Ransomware Deployment Phase
During the second phase, the deployment of a ransomware payload can take several minutes or longer depending on several factors, including the robustness of the existing cybersecurity system. According to Microsoft’s 2022 Digital Defense Report, an hour and 42 minutes is the median time for an attacker to start moving within an organization’s network once a corporate device is compromised.
Cybersecurity Strategy for Organizations
To effectively combat and prevent attacks of this nature, organizations need to adopt an enduring cybersecurity strategy that shifts their mindset towards comprehensive protection. The primary goal is to disrupt attackers' progress from the pre-ransomware phase to the ransomware deployment phase.
Enterprises should consistently and assertively apply security best practices to their networks, aiming to mitigate various classes of attacks. The complexity of human decision-making in ransomware attacks often generates multiple security alerts that may appear unrelated, leading to alert fatigue and delayed responses. Security operations centers (SOCs) can overcome this by identifying trends and grouping alerts into incidents to gain a broader perspective. By doing so, SOCs can effectively address alerts using hardening capabilities, such as attack surface reduction rules. These measures not only reduce alert volume but also serve as a barrier to prevent attackers from gaining access to networks.
Sustaining a continuous high standard security posture and network hygiene is paramount for organizations to safeguard themselves against human-operated ransomware attacks. Proactive and comprehensive protection remains the key to thwarting such threats effectively.
Defense Strategies Against Ransomware
Below is a list of things that organizations can do to better defend against ransomware attacks:
• Mitigate SOC alert fatigue through network hardening, which reduces the volume of alerts and preserves bandwidth for addressing high-priority incidents.
• Give priority to strengthening cloud security measures.
• Minimize the attack surface by eliminating potential vulnerabilities.
• Enhance the security of internet-facing assets and gain a clear understanding of your network perimeter.
You can click here to learn more about Microsoft’s forensic analysis of a BlackByte 2.0 ransomware attack chain.
Take a look at the next section to learn about the impact of ransomware on a food distribution company.
Ransomware Attack Review: Lessons from Sysco
Despite the fact that finance, education and healthcare are the top 3 industries being targeted by cyberthreats and ransomware, this does not mean that other industries can breathe a sigh of relief regarding their cybersecurity vigilance.
In May 2023, Sysco, a leading global food distribution company, confirmed that its network was breached earlier in March by hackers who stole sensitive data from their North American division.

Here is a short timeline of the cyberattack:
- January 14, 2023 – Cyberattack initiated by hackers who gained access to Sysco's system to download sensitive company data. This would have started with a pre-ransomware phase mentioned in the previous section before the hackers went through the 7 stages of a ransomware attack.
• The cyberattack already started before January 2023 as the hackers had likely been scouting Sysco's existing systems for any digital vulnerabilities. Historically, scouting was used by armies to observe their enemy’s movements before initiating an attack. Although scouting is not “the attack itself”, it is a serious indication that an attack is already underway (on the intelligence side before it is manifested physically).
- March 5, 2023 – Sysco becomes aware of the cybersecurity breach and starts its investigation into its impact on their systems.
- Having the right, updated threat detection systems in place is vital to addressing a cyberattack the moment it happens or stopping a data breach before it begins. The longer the time between a cyber breach and its detection by the victim, the more time for a hacker has to plunder or encrypt valuable company data. An additional risk is that a hacker can also create a digital “back door” within their victim’s systems which can then be used for future data theft.
- A critical point to note is that it took a shocking 50 days for Sysco to realize that their systems had been breached more than 1 month prior!
According to a filing with the Maine Attorney General's Office, this data breach impacted 126,243 individuals whose names and other Personal Identifiable Information (PII) were exposed together with Social Security Numbers.
Although Sysco also hired a cybersecurity firm to help examine the incident and mentioned that this cyberattack has not impacted its business operations and customer service, this unfortunate event is a reminder of the importance of maintaining strong cybersecurity measures to protect organizational and personal data.
Don't wait until it's too late - take action now to bolster your organization's cybersecurity.
Lessons from Sysco's Cybersecurity Incident
Lesson: Don't wait until it's too late - take action now to bolster your organization's cybersecurity.
AI in Microsoft Sentinel swiftly identifies genuine ransomware threats by leveraging vast amounts of data and analyzing trillions of signals daily, reducing false positives and noise from legitimate events. Empowering security teams with pre-built queries and integrated automation, Sentinel accelerates proactive threat hunting and response, providing a comprehensive visualization of attacks and enhancing overall cybersecurity effectiveness.
Implementing robust security measures, such as multi-factor authentication, encryption, and ongoing security training, can help prevent cyberattacks and minimize potential damage. Keep your software and systems up to date with the latest patches and updates, and regularly conduct security audits to identify any vulnerabilities.
By taking proactive measures, you can safeguard your organization's priceless data and avoid devastating security breaches. Remember, the cost of a cyberattack is not just financial - it can also cause reputational damage, loss of customer trust, and legal ramifications. Prioritize cybersecurity today to protect your organization's future.

Microsoft Security Copilot: AI Meets Cybersecurity Excellence
In a fast-paced cyber landscape, defenders need a force multiplier to combat the ever-evolving threats of ransomware. That's where Microsoft Security Copilot, now under development, comes in, revolutionizing the defense game with the prowess of AI. By sifting through trillions of signals every day, its advanced machine learning capabilities support IT security teams with an unparalleled advantage, filtering out false positives and noise caused by legitimate events, empowering them
Designed to boost the capabilities of security teams, Microsoft Security Copilot comes prepared with pre-built queries cultivated from years of security expertise. This extraordinary accelerator unlocks the potential for proactive threat hunting, equipping defenders with the tools to stay ahead of even the most sophisticated adversaries. With a prioritized list of alerts and instantaneous analysis of thousands of security events, Copilot paints a comprehensive picture of each attack's scope.
Features of Microsoft Security Copilot
Here are some of the features of the upcoming Microsoft Security Copilot:
• Threat Hunting: Uncover potential vulnerabilities and exploits within your organization by thoroughly examining each asset for signs of a breach.
• Security Reporting: Generate concise reports summarizing events, incidents, or threats within minutes, customizable for different audiences.
• Incident Response: Swiftly identify and assess ongoing attacks, and receive actionable instructions for remediation based on proven tactics from real-world security incidents.
 But that's not all – Microsoft Security Copilot takes cybersecurity to new heights by seamlessly integrating automation and orchestration into security operations. This intelligent fusion streamlines workflows and automates common tasks, enabling defenders to respond to threats at lightning speed.
But that's not all – Microsoft Security Copilot takes cybersecurity to new heights by seamlessly integrating automation and orchestration into security operations. This intelligent fusion streamlines workflows and automates common tasks, enabling defenders to respond to threats at lightning speed.
Embracing Microsoft Security Copilot is a bold move towards an impregnable ransomware defense, elevating the overall effectiveness of cybersecurity measures. With the might of AI on their side, organizations will be equipped to safeguard their digital realms like never before, ready to face the challenges of the future head-on.
Interested in seeing how It works? Click the link to watch the Microsoft Security Copilot demo.
Conclusion
Discover the power of AI and cybersecurity excellence with Microsoft Security Copilot, a true game-changer in the relentless battle against ransomware attacks. By proactively hunting for vulnerabilities, summarizing security events, and rapidly responding to incidents, Security Copilot empowers defenders with unparalleled tools to safeguard digital assets effectively.
Concerned about your current cybersecurity? Contact us today to fortify your organization's digital defenses and take a resolute stand against cyber adversaries. Stay vigilant, stay secure!
Tags:

August 01, 2023
.png?width=500&height=500&name=cyber%20security_110110543%20%5BConverted%5D%20(3).png)



Comments