As applications become more cloud-based, cyber threats to cloud networks are increasing within organizations. As a tech professional, you want to be able to protect your endpoints from threats that bypass your firewalls and hack your cloud networks. With the increasing popularity of remote work, your business needs to consider protecting your employee’s endpoints, such as desktops, laptops, and mobile devices, wherever they may be in the world.
So, how does your organization ensure that your endpoints and digital assets are protected from cybercrimes? This blog will cover securing your endpoints and security solutions to protect your digital assets.
In this blog, you will find:
Securing Endpoints for the Modern World
The Big Question - Is My Company Safe from these Cyberattacks?
How to Protect your Digital Asset Endpoints
Microsoft Tools that Can Help Protect your Endpoints
Which Microsoft Tools tan Help Protect your Endpoints?
How does Microsoft Sentinel Protect my Endpoints?
Securing Endpoints for the Modern World
In our modern-day world, it is difficult to identify what kind of threats your endpoints may be exposed to. As your organization is faced with constant threats every day.
Here are some examples of threats that you may face in the modern landscape:
🔒 1. Crypto-lockering/Ransomware - This is the most common cybercrime that happens to multiple businesses. In this situation, cyber criminals will gain illicit access to your environment allowing them to encrypt important business files. Your organization may be threatened to pay a ransom, usually via cryptocurrency. If the ransom isn’t paid, your business files may never be recovered as a result of the attack.
💻 2. Advanced Persistent - Malicious parties will lurk in your business network, completing a long term reconnaissance behind the scenes. This type of cyberattack is particularly dangerous as they can build and steal data undetected. Therefore, your business may be under attack for years until the criminals decide to reveal themselves.
📑 3. Malvertising/Adware - This method of cybercrime is common with our everyday browsing. This threat typically presents itself on websites and seeks to direct the end user to scam websites or nefarious web portals where worse malware can be deployed. Be careful what links or ads you click on when browsing the internet.
📧 4. Phishing - For organizations, phishing is quite a common cyberattack. Using social engineering and email attacks, hackers can gain access to your company workstations or mobile devices which allows easier access to crucial sensitive information on your company network.
📉 5. Data Loss and Theft - Hackers will often use less malicious means to seek out and steal critical data such as financial information, client data and company intellectual property to use for their own unlawful purposes.
The Big Question - Is My Company Safe from these Cyberattacks?
The most common question that every organization asks, “is my company safe from cyberattacks?” The answer is no. The move to more Cloud-based systems, combined with a more mobile or remote workforce means that the border of your digital estate has been pushed beyond the physical boundary. Therefore, let us address the issue - is your company safe from cyberattacks?
1. Cellphone Vulnerability
Nowadays cellphones are more commonly targeted in hacks, such as stealing a company’s client info list. Therefore, monitoring what applications are installed on mobile devices is a key step to prevent a future cyberattacks.
2. Small Businesses
You might think hackers won’t bother to try and cyberattack a small business, but they see it as a weak point as most small businesses don’t have strong security as compared to bigger enterprise corporations. Therefore, it's recommended no matter the business size that you should investigate ways to prevent Cyberattacks from happening.
How to Protect you Digital Asset Endpoints?
It can be difficult to determine exactly what tools your business needs to protect your endpoints. With any security solution, there are always a ton of options available which can make choosing the right one overwhelming. We have narrowed the selection down to two solutions that can help your organization protect your endpoints.
🌟Legacy AntiVirus Solution - Legacy AV systems utilize a daily list of threats that are utilized to analyze any potential threat in the list that is currently on the system or incoming. However, this showcases the downside to Legacy AntiVirus as it would not prevent a crypto-lockering attack from encrypting all of your critical workplace files.
📍The Endpoint Detection Response - An EDR solution should cover all devices under your company’s umbrella such as Mac OS, Windows, iOS, Android and other devices. If a device is enrolled in Defender for Endpoint, the device can be anywhere in the world, and it can forward information directly to the cloud security app, providing 24/7 instant behavioral analysis using cloud-based services to prevent most cyberattacks from occurring.
Which Microsoft Tools that Can Help Protect your Endpoints?
Microsoft offers a variety of tools that can help lower cyberattacks and increase monitoring within your organization. It is a matter of choosing the right tools that work best for your business.
We recommend three tools that your organization can choose to implement.
1. Microsoft Defender for Endpoint
- Defender for Endpoint is monitored via the cloud 24/7 to detect irregularities in network systems which will prevent a Cyberattack from happening in ways that a Legacy AV simply cannot. This solution does not rely on a definition file.
- It has full compatibility to run across all desktop and mobile devices such as Windows, Mac OS, iOS and Android.
- This tool is possibly already bundled with your current Office 365 license subscription, if not a different license is required.
- It provides the best fit with Microsoft’s ecosystem, ensuring ease of use and compatibility.
2. Microsoft DLP (Data Loss Prevention) for Endpoint
- Allows you to audit and manage activities users partake in on sensitive files that are physically stored on Windows or Mac OS machines.
- Creates a powerful layer of protection for local business data. Helps to retain control over company IP and client information while staff is working from home.
- Provides auditable records of business-critical files and data.
- Allows your company to understand how a cyberatttack happened and what impact it had on your business.
3. Microsoft InTune
- With Microsoft InTune, you will be able to create strict end user policies that will apply standards and govern your endpoint devices on your business network
- Deploy Microsoft Defender products automatically to all machines linked to your domain to ensure the best possible security
- Control access with specific policy rules for your company resources and data to help reduce valuable data loss
- Apply and force policy standards across your whole workplace environment
- Manage changes to applications, policies, and device access across your environment from a single pane solution which allows for ease of use to submit any changes that need to be addressed
- Receive instant alerts when a device falls out of standard and pre-configure automated activities for when it does unfortunately happen
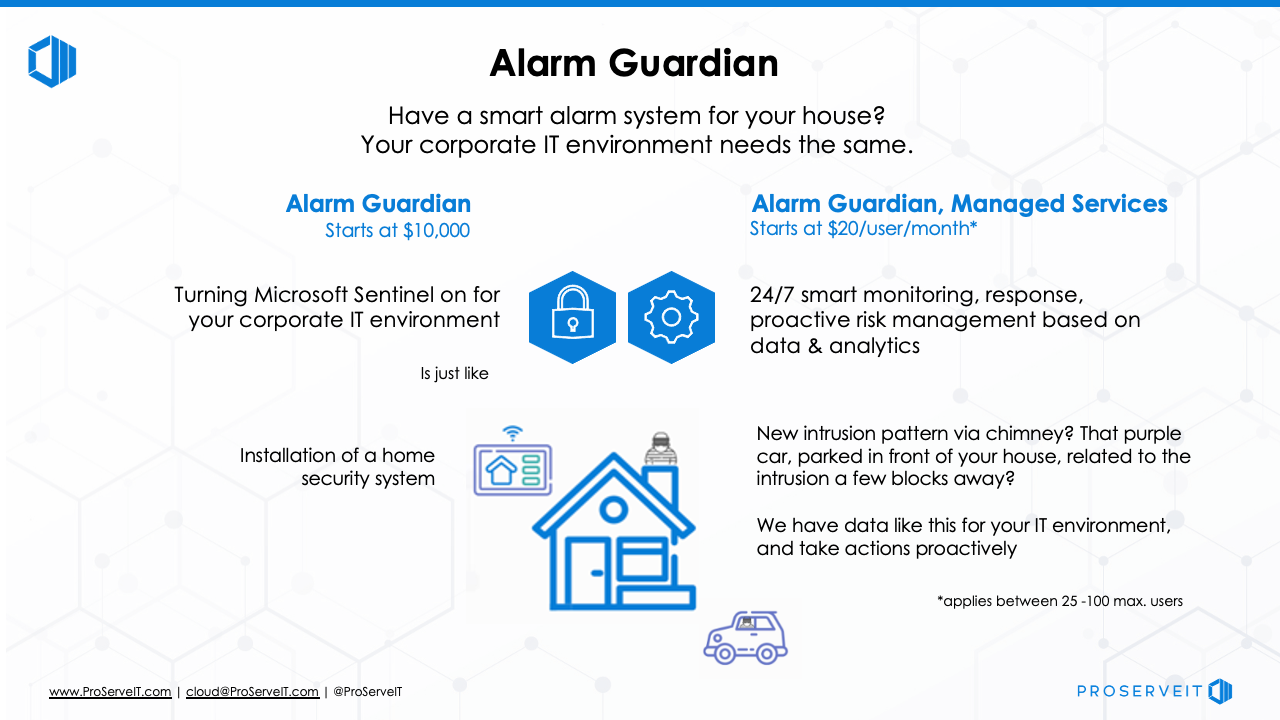
Alarm Guardian Uses Microsoft Sentinel to Protect your Organization
Microsoft Sentinel, a Cloud-native security information and event manager (SIEM) platform helps your organization to filter legitimate events happening in your network from viable threats. Learn more about Alarm Guardian.
How does Microsoft Sentinel Protect my Endpoints?
Ultimately, everything comes down to choosing the right tools for your business. With Microsoft Sentinel, we are able to develop automated responses for threat protection.
What are the key features of Microsoft Sentinel that can be implemented in your business?
📈 1. Data collection from different sources throughout the cloud - this includes data integration with existing tools and thorough analysis of your data security environment.
🏗️ 2. Built-in user and entity behavioral analytics (UEBA) help in identifying threats and their potential impacts.
📍 3. Detects suspicious behavior, compromised assets and its impact radius. With this, security teams can further prioritize their investigation and incident handling.
ProserveIT offers a solution that is built around Microsoft Sentinel called Alarm Guardian.
🛎️ This service is supported by ProServeIT’s Security Operations Center’s security analysts and security engineers on a 24 x 7 x 365 basis.
⏰ Alarm Guardian will provide real-time analysis and response to security generated by your servers, devices, firewalls and network device users. It is much like an alarm system that scans for suspicious activity, and alerts you to potential threats within your network.
If you are looking for ways to increase your security and protect your digital identity in a cost-effective and efficient way, then ProServeIT’s Alarm Guardian could be the security solution that you are looking for. Learn more about Alarm Guardian here, then contact us to get started today!
 Content from: Cybersecurity Framework Webinar Series by George Abou-Samra
Content from: Cybersecurity Framework Webinar Series by George Abou-Samra
Edited by: Rachel Nguyen and Betty Quon
Tags:
June 30, 2022

Comments