What Is IT Security & Why It Matters More Than Ever
Security and safety are the number one priority for your organization. Without proper tools, the risk of cyberattacks can lead to the downfall of your business. As we move forward to cloud-based servers, protecting important information has become increasingly difficult. Therefore, your organization must be able to protect your overall security posture to prevent cyber crimes from stealing your digital identity and data.
In this blog, we will cover the challenges that come with traditional security measures and how to improve your security with a three-step approach. As well, we will cover Microsoft Sentinel as a solution that can monitor your overall cyber security posture.
In this blog you will find:
3 Challenges Organizations Face with Cyber Security
Three-Step Phased Approach to Cyber Security Posture
Why use Microsoft Sentinel for my Organization?
Alarm Guardian uses Microsoft Sentinel to Protect your Organization
3 Common Challenges Organizations Face with Cybersecurity
Today, organizations are faced with the difficult task of trying to protect their expanding digital estate from increasing cyber threats. With the rise of COVID-19, the move to cloud-based servers and a mobile workforce has pushed the border of your business’ physical network. In other words, users working from anywhere in the world are not tied down to their office space. Therefore, sharing sensitive information through cloud-based models has increased with remote work. With the modern IT era, organizations cannot rely on traditional security operations to protect their information and digital assets. So, what are some common challenges organizations face with traditional security today?
😈 Sophistication of Threats
Attack techniques are getting complex and difficult to pinpoint. They are frequent and happen extremely fast. A typical attack can span across various resource types, for example, it might start from an email address, proceed to an endpoint, spread to a cloud service or to a database and involve multiple user accounts.
⏰Alert Fatigue
When a breach happens, security teams can be put under pressure from the expanding range of the attacks and not knowing what security tools they need. Therefore, multiple alerts can come from disconnected products which can cause alert fatigue. To avoid alert fatigue, your organization must prioritize certain alerts and enable investigation and hunting across your entire data set.
⚠️Breach Investigation
Breach investigations are complex and time consuming. When there’s a security breach, every second counts and security personnel are handling a threat that might jeopardize their organization. The clock is ticking fast, but investigation requires highly skilled security analysts and can often take days or weeks to solve. The shortage of security talent makes this problem even worse, and the need for skilled security professionals has greatly increased with time and supply cannot meet current or future demand.
Three-Step Phased Approach to Cybersecurity Posture:
Security is a process. With the challenges listed above, we recognize that it can take a significant time to solve and prevent cyberattacks. There is no way to eliminate every single threat that will attack your organization however, we can reduce the chances of cyberattacks. With this three-step phased approach to security, we can show you how to protect your overall cyber security posture.
1. Assess the Environment
Perform security assessments to identify gaps, areas of improvement, and create a security roadmap. You must be able to understand the risks involved with each identified gap so you can make an informed decision on what to do with that risk. Do you want to mitigate it? Do you want to accept it, or do you want to transfer it to a third party? By identifying the gaps, part of your assessment should be a security profiling exercise to help determine your organization's current maturity level. By building a security roadmap, your organization can identify what security measures need to be deployed.
2. Protect the Environment
Deploy the various Microsoft security technologies to close gaps identified in the assessment phase. Gaps identified can range from areas such as identity, access management, data, email, endpoint security and finally application security. Identify everything that needs the utmost security to ensure your organization is protected to the best of its ability.
3. Monitor the Environment.
Monitor the environment using SOC (security operations centre) as a service such as ProServeIT's Alarm Guardian. Your organization needs to be able to detect such activities before events progressively get worse. Utilizing ProServeIT's Alarm Guardian with Microsoft Sentinel allows for 24 x 7 x 365 monitoring to ensure your organization's security safety.
These three-step approach can be viewed as a cycle. Every time a change happens within your environment, whether it is adding a new service, new server, or a new application, you want to assess that service to ensure that it is secure. Therefore, when the gaps are identified, you can protect and monitor those services to prevent cyberattacks.
Want to protect your digital end-users? Download this eBook(Safe Computing Best Practices for End-Users) to learn practical tips and protect your organization from a cyber-breach.
Why use Microsoft Sentinel for my Organization?
To protect your overall cyber security posture, Microsoft has a wide range of tools that can help protect your organization’s environment. In this case, we recommend the use of Microsoft Sentinel.
Microsoft Sentinel is a SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation and Response) application that is a scalable cloud native solution which allows your business to analyze data in real time.
What is SIEM and SOAR?
SIEM allows analyzing of event data in real time to detect early breach attempts. Therefore, it allows logs to be stored for any future use such as providing it to a regulator body if necessary
SOAR allows streamlined security operations with playbooks. In this case, playbooks allow the use of automation where specific security events can automatically be handled without any human intervention. For example, if a user is logging into an account from a different country, playbooks can be set-up to automatically reset the user’s password to prevent a breach. Playbooks can be highly effective and easy to change and set up according to your organization’s needs.
What is Microsoft Sentinel?
Microsoft Sentinel works with various cloud platforms to collect, analyze, and prevent malicious attacks on your organization in most cases utilizing automation from playbooks for a faster and more efficient response. How does Microsoft Sentinel work as an end-to-end solution for security operations?
📈 It collects data.
A simple ingestion process can be developed using either Microsoft or third-party data connectors.
📍 It detects security incidents.
Microsoft Sentinel creates analytic rules, some guided by Artificial Intelligence, to alert you to security incidents. Analytic rule types include fusion, machine learning behavioural analytics, Microsoft security analytics and scheduled queries.
🕵️ It investigates thoroughly.
Microsoft Sentinel helps you to understand the scope of the incident and finds the root cause of potential security threats.
📶 It responds efficiently.
Microsoft Sentinel automates workflows by creating “playbooks” using logic apps.
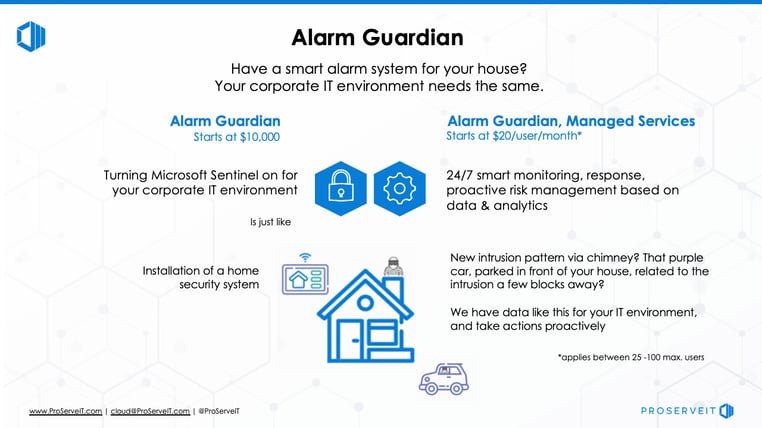
Alarm Guardian uses Microsoft Sentinel to Protect your Organization
ProServeIT offers a solution that is built around Microsoft Sentinel called Alarm Guardian.
🛎️ This service is supported by ProServeIT’s Security Operations Centre’s security analysts and security engineers on a 24 x 7 x 365 basis.
⏰ Alarm Guardian will provide real-time analysis and response to security generated by your servers, devices, firewalls and network device users. It is much like an alarm system that scans for suspicious activity, and alerts you to potential threats within your network.
If you are looking for ways to increase your security and protect your digital identity in a cost-effective and efficient way, then ProServeIT’s Alarm Guardian could be the security solution that you are looking for. Learn more about Alarm Guardian here, then contact us to get started today!
Content from: Cybersecurity Framework Webinar Series by George Abou-Samra
Edited by: Rachel Nguyen and Betty Quon
Tags:
July 22, 2022

.png?width=500&height=500&name=cyber%20security_110110543%20%5BConverted%5D%20(3).png)



Comments