What are Cloud vulnerabilities and what can Microsoft Cloud App Security do to help mitigate them?
At ProServeIT, we have seen a lot of potential for Cloud vulnerabilities within organizations. With the influx of Software as a Service (SaaS) applications, like Dropbox, Google Drive, Salesforce.com, and more, it can be tough to keep a handle on what data is making its way out your front door. Even worse is when these applications are installed on your company IT infrastructure without your knowledge or consent by employees who are only trying to make their jobs easier, but don’t quite realize the implications of what they’re doing – this, by the way, is called Shadow IT.
To help with minimizing Cloud vulnerabilities, Microsoft Cloud App Security is, in our opinion, one of Microsoft’s best kept secrets. It resides within the Azure AD Premium product, and provides visibility into cloud apps that are residing in your environment, either with or without your knowledge. In this blog, we’re going to provide you with a detailed overview of Microsoft Cloud App Security and how it can help you to minimize the Cloud vulnerabilities in your organization.
What is Microsoft Cloud App Security?
First thing’s first. Just what exactly is Microsoft Cloud App Security?
Simply put, Microsoft Cloud App Security is a comprehensive solution that can help your organization take full advantage of Cloud applications, but also keeps you in control by providing you with improved visibility into any activity happening within your IT environment.
Built-in tools that natively integrate with other leading Microsoft solutions can help you assess your risks, investigate suspicious activities, uncover shadow IT within your organization, stop threats in their tracks, and more.
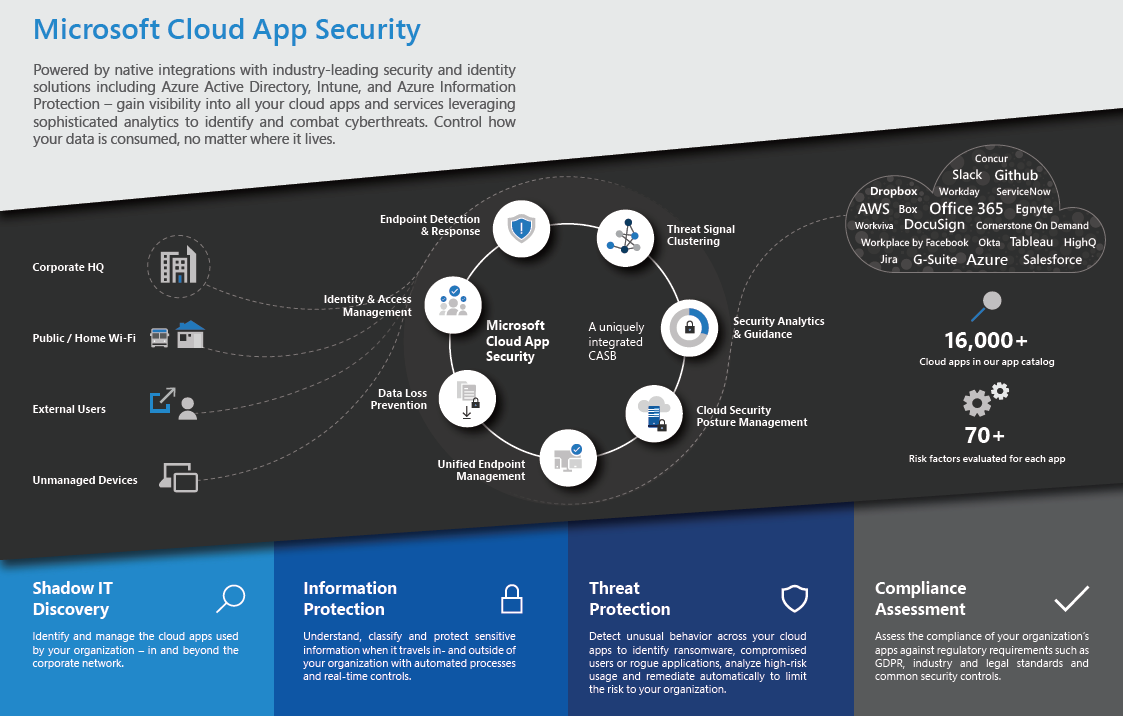
Microsoft Cloud App Security covers four main areas:
- Shadow IT Discovery
- Information Protection
- Threat Protection
- Compliance Assessment
What does Microsoft Cloud App Security Do?
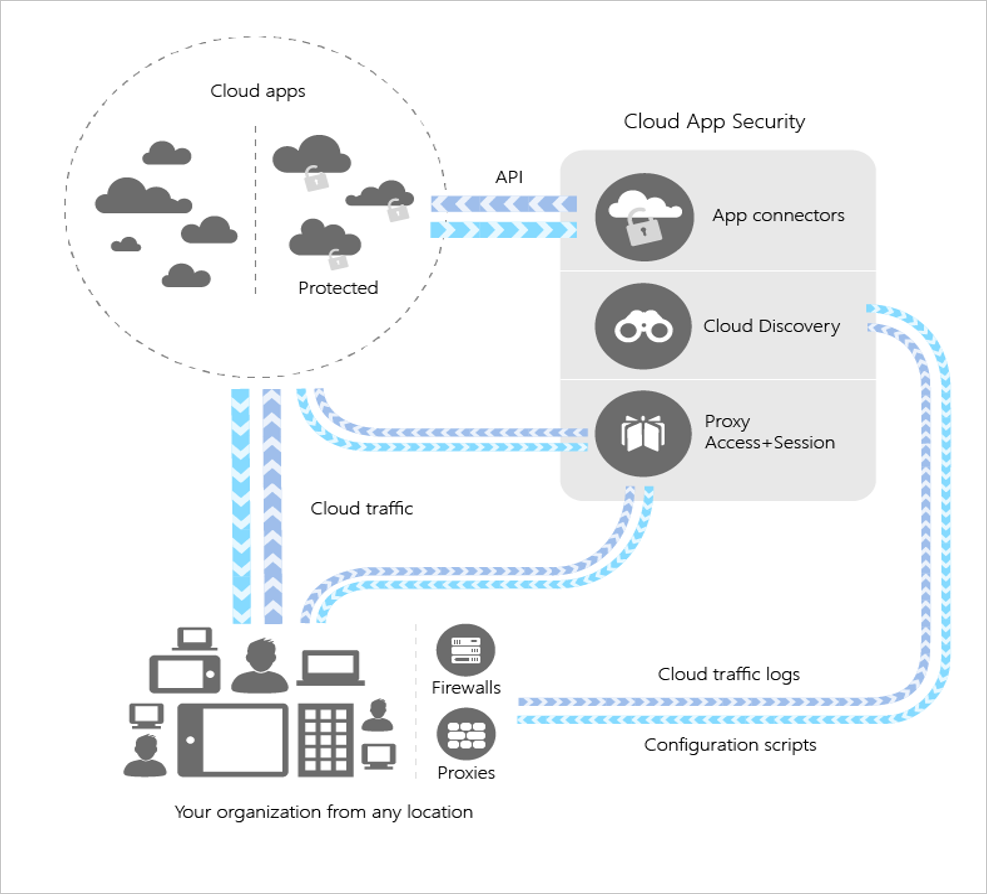
Well, Microsoft Cloud App Security helps you achieve visibility into your IT infrastructure in the following ways:
- You can use Cloud Discovery to map and identify your Cloud environment and the Cloud apps that your organization is using. This includes shadow IT reporting.
- You can sanction and unsanction apps through the Cloud App catalogue, which has ranked and scored over 16,000 Cloud apps. Microsoft Cloud App Security can rate the risk for the apps you’re seeing in your environment, based on regulatory certifications, industry standards, and best practices.
- Microsoft Cloud App Security will help you set, monitor, and revise policies within your organization.
- You can monitor and control your data in the Cloud.
- You’ll be able to detect atypical or abnormal use, which could mean there’s a potential security incident in progress.
So, by running Microsoft Cloud App Security in your organization, you can create a snapshot of the Cloud apps that your organization is using and gain valuable insight into what Shadow IT could be residing within your environment. Plus, Microsoft Cloud App Security will also provide you with a rank of how secure each of your Cloud apps are, and even create policies that can help define your user’s behaviour in the Cloud, such as detecting risky behaviour, limiting downloads, setting rules that force data being stored in the Cloud to be encrypted in transit, and more.
Why Should You Care about Cloud Vulnerabilities?
Let’s take a look at a scenario that is quite common in many organizations today:
Tim is one of your Business Development Managers. He’s working on landing a major deal for your organization that has the potential to bring in a quarter million in revenue in the first half of the year, with residual revenue throughout the next several years. Tim wants to work on putting together the Statements of Work for this potential client at home, but he doesn’t have a USB with him to copy the content over. So, to work around this, Tim installs Dropbox on his computer and uses his Dropbox account to drag-and-drop the files he needs into it so that he can work on it from home.
Now, when you look at the above scenario, three things should be perfectly clear to you:
- Tim is a diligent employee who wants to be able to land this deal.
- Tim is trying to make his job easier.
- Tim has just shared data over a well-known, reputable company’s software.
Dropbox is not, by any stretch of the imagination, evil. They are a reputable company and, for many organizations, they are a viable solution to sharing content between team members. But in the scenario above, Tim’s use of Dropbox has created an unnecessary Cloud vulnerability that could be exploited by cybercriminals to gain access to your valuable data.
That’s because, in this scenario, Dropbox has become Shadow IT – an application that Tim downloaded without your (or your IT department’s) express authorization to be in your IT infrastructure. Nobody from your organization knows that Dropbox has been added to your environment, therefore nobody is monitoring how secure it is, and, more importantly, nobody knows what corporate data is being shared across it.
Unfortunately, Tim’s story is incredibly common. In fact, while the average CIO would estimate they have 51 Cloud services running in their organization, the actual number is 730 (according to Cisco’s Shadow IT report). That’s a lot of Shadow IT, and a lot of Cloud vulnerabilities that are threatening your organization’s security!
Microsoft Cloud App Security, however, can help you discover and control the use of Shadow IT in your organization, so you’ll always know what Cloud apps are running, which ones are posing a security risk to the organization, and what you can do about it.
Get Started with Cloud App Security Today
So, how do you get started addressing your Cloud vulnerabilities? At ProServeIT, we use Microsoft Cloud App Security as the basis for our Shadow IT Assessment . This assessment can help you to not only understand what Shadow IT is currently running in your environment, but also provide you with a risk profile for your organization, and help you to build out a plan around what tools or processes you need to put into place in order to reduce your risks.
ProServeIT’s Shadow IT Assessment has many benefits:
- We’ll help you eliminate concerns over unauthorized access to corporate data.
- You’ll be able to understand possible data leakage points and other security risks that are inherent to Shadow IT.
- You’ll identify users within your organization who are using Shadow IT, and you can use what you’ve learned to build a plan to educate all your employees on the dangers of Shadow IT.
Interested in doing a Shadow IT Assessment for your organization? Contact us today to get started!
Or, if you’d like to hear more about the topic of Shadow IT, join our upcoming webinar on the potential dangers of Shadow IT for your organization!
Hosted by ProServeIT’s cybersecurity experts, this webinar will help you increase your organization’s security posture by showing you why Shadow IT is so potentially dangerous for your organization and what you need to do to mitigate it.