Welcome to the Cybersecurity Course
Dive into cybersecurity's dynamic world with our curated webinar series. Gain unparalleled insights to bolster your skills and knowledge in this ever-changing field.
📍Bonus webinars:
Webinar 01: Revolutionize Your Company's Device Management with Microsoft Intune
Semester 1 classes:
Class 01: Simplifying Your Security Journey
Class 02: Microsoft's Zero Trust Model
Class 03: Ransomware as a Service: How to Protect Your Organization
Semester 2 classes:
Class 01: Protect Against Phishing Scams and Identity Theft
Class 02: The Good and Bad of Artificial Intelligence in Cybersecurity
Bonus Class: Improve your Insurability and Protect your Business with Cybersecurity
These webinars are designed for IT leaders and IT professionals. Register for the course to receive the password to watch the recordings below.
Bonus Webinars
🍰 Webinar 01: Revolutionize Your Company's Device Management with Microsoft Intune
Cybersecurity Bonus Class has happened!
Register for the course to receive the password for the recording.
In an era where mobile devices, remote work, and data security are top priorities, Microsoft Intune is critical for your organization to maintain control, increase productivity, and safeguard your valuable data, making it a cornerstone of modern IT management and security strategies.
This webinar will explore how you can secure your hybrid and frontline workforces across platforms, leverage AI-based recommendations, reduce complexity, and cut costs at the same time.
Join us to learn how a centralized hub with real-time controls can help you to easily oversee, manage, and fortify security on all your devices and endpoints.
Classes from Semester 1
🔒 Class 01: Simplifying Your Security Journey
Cybersecurity Class 01 has happened!
Register for the course to receive the password for the recording.
There is a myriad of complex cybersecurity products available on the market. You know your organization is vulnerable, but you may not know where to start. Simplify your security journey with our 3-step process: assess – protect – monitor.
The journey starts with identifying your security risks and determining where you can be attacked. What could happen if your information is stolen or released? Once you’ve identified your risks, you can decide how to mitigate them and close your gaps. You may want to prioritize risks to your sensitive data or risks to your business reputation. Once you have remedied your major risks, the last step is to monitor and ensure that new evolving threats are addressed as they arise.
Cybersecurity is a continuous process and it’s never too late to get started. Learn how to deploy a simple 3-step process to start you down the path to digital security.
📋 Class 02: Microsoft's Zero Trust Model
Cybersecurity Class 02 has happened!
Register for the course to receive the password for the recording.
Today’s organizations need a new security model that more effectively adapts to the complexity of the modern environment. Securing your digital assets requires Zero Trust. A Zero Trust security model treats every activity as a threat unless you can prove that it isn’t. Microsoft has been building their world-class cybersecurity model on this principle. In the Microsoft environment, every activity, including activity within your organizations, is challenged as a potential threat.
Start with a self-assessment to get recommendations customized for your organization. Explore methods you can use today to stop malicious activities before they can do damage. Align your Zero Trust investments to your current business needs and improve your organization’s security posture.
🛡️ Class 03: Ransomware as a Service: How to Protect Your Organization
Cybersecurity Class 03 has happened!
Register for the course to receive the password for the recording.
Did you know that there is a cybercrime gig economy out there? Rather than carrying out cyberattacks, some criminals are learning that there’s less work and less risk when they rent or sell their tools to others for a portion of the illicit profits. How can you protect your organization against sophisticated nefarious activities such as theft of highly valuable data, threats to publish your data or repeated extortions for payment once a cybercriminal gets access to your environment?
Learn how you can harden your environment against ransomware threats. Reduce your attack surface by addressing security blind spots, modernizing your legacy configurations, removing easy entry points into your environment, and employing sophisticated tools that can detect and respond to imminent attacks.
Classes from Semester 2
👤 Class 01: Protect Against Phishing Scams and Identity Theft
Register for the course to receive the password for the recording.
Are you tired of falling victim to phishing scams and identity theft? Protect yourself and your personal information with our comprehensive guide on identifying and avoiding these malicious attacks.
Our experts will share the latest tactics used by cybercriminals, real customer stories, and provide you with practical tools and strategies to safeguard yourself and your personal information with data protection solutions and data breach prevention best practices.
🤖 Class 02: The Good and Bad of AI in Cybersecurity
Cybersecurity Class 02 has happened!
Register for the course to receive the password for the recording.
Are you curious about the potential of Artificial Intelligence (AI) in cybersecurity, but also concerned about the potential risks?
Join us for an enlightening session where we'll dive deep into the good and bad of AI in cybersecurity. From its ability to quickly detect and respond to cyberthreats to its potential for misuse, this class will provide you with a comprehensive understanding of the impact of AI on cybersecurity. We’ll share a real-life scenario to illustrate what can happen.
⭐ Bonus Class: Improve Your Insurability and Protect Your Business with Cybersecurity
Register for the course to receive the password for the recording.
What assets are most valuable to your business? For most organizations, it is their digital assets such as their customer data, financial data and other documents and assets that are vital to run their business.
Cybercrimes targeting these assets are becoming ever more prevalent and this makes investment in the best-in-class cybersecurity technologies a necessity for all businesses regardless of their size or industry. This also has increased the need for a proper cybersecurity insurance policy.

About the Instructor
George Abou-Samra
Principal Consultant and Security Practice Lead, ProServeIT
George Abou-Samra is a Principal Consultant and Security Practice Lead at ProServeIT. As Security Consultant, George's primary focus revolves around ensuring that ProServeIT's customers and organizations in general are made aware of the increase in cybersecurity risks, as well as providing guidance on what to do to better secure their organizations from threats and bad actors. George's extensive technical background is supplemented by his expertise in white-hat hacking, gaining a better understanding of the methods that hackers would employ to break into a customer's environment, and utilizing that knowledge to better protect the customers he works with on securing vulnerable points of entry. When George isn't working, he enjoys spending time with his family, playing basketball, and hiking through the beautiful trails in Ontario and Canada.

About the Instructor
Joy Fajardo
Brand Experience Manager, ProServeIT
Joy Fajardo lives to make an impact! A marketing native and social media influencer, Joy has an unshakable passion for helping organizations thrive with both inbound and outbound activities by using the right technologies! Joy began her career in Singapore, working as a marketing specialist whose responsibilities included educating, influencing, and affecting client decisions, while also helping to bridge the gap between technical data, branded content, and consumers. After moving to Canada in 2019, Joy joined ProServeIT's marketing team to support inbound and outbound sales and marketing initiatives. She'll draw from her vast experience to help you increase awareness for your cause and raise funds in the most resource-efficient way possible.
Outside of work, Joy is a crusader for proper nutrition for children, especially in the Philippines, where she's from. She also runs a successful YouTube channel in her native language that provides valuable immigration information for others considering Canada.
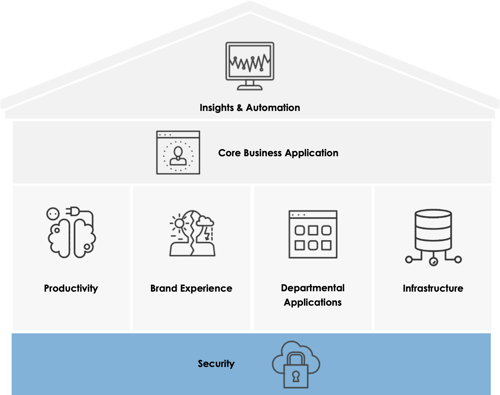
Where does the Cybersecurity Course Fit within Your Technology Strategy?
Every house needs a solid foundation before the main floor is built.
What it means to have security as the foundation of your Technology Strategy Framework is, as you’re making technology investment decisions, you want to make sure that the new technologies are secured by design and that they’re not going to introduce any additional risks to your business.
Join George to understand better on how you can create that strong foundation for your Technology House.
To learn more about each room of The House, have a look at our blog, The CEO’s Technology Strategy Framework.
© 2020 ProServeIT | About Us | Privacy Policy | Terms of use






