By: Eric Sugar, President, ProServeIT Corporation
Cyber risk management needs to be top of mind for every executive out there.
Do you have a cyber risk management policy in place in your organization? Are you aware of what the cyber risks are, not just as the CEO of your company, but also from a personal standpoint? Do you want to learn about how to improve your security habits and behaviours? These are all very important questions to consider. Read on to understand a bit more about cyber risk management.

Cyber Risk Management Starts with Understanding the Need for Cybersecurity
We’re living in some very turbulent times. The threats to businesses have become quite sophisticated in nature. Gone are the poorly-written, grammatically-atrocious emails from a prince whose wealth has been tied up in legal proceedings and, if you just send him your banking information, he’ll reward you with a million dollars.
Nowadays, threat actors are becoming much more conniving, convincing, and devious. Mimicking banks, IT companies, cell phone companies, utilities, and even the Canadian Revenue Agency, threat actors today will do whatever it takes to scare you into clicking on malicious links or providing your personally identifiable information.
Here are some sobering cybersecurity statistics that Microsoft provided in their 2016 Trusted Cloud Survey:
- One in three executives admit that their company doesn’t have an end-to-end security strategy currently in place.
- Less than 25% of executives have been able to fully fund the necessary investments to protect themselves and their organization from modern security threats.
- The average organization will face 186 targeted cyberattacks every year.
- Only 21% of executives believe they’re fully prepared for today’s cybersecurity threats.
These are concerning statistics that show that cybersecurity isn’t as top of mind as it perhaps should be.
Cyber Risk Management: Know the Risks
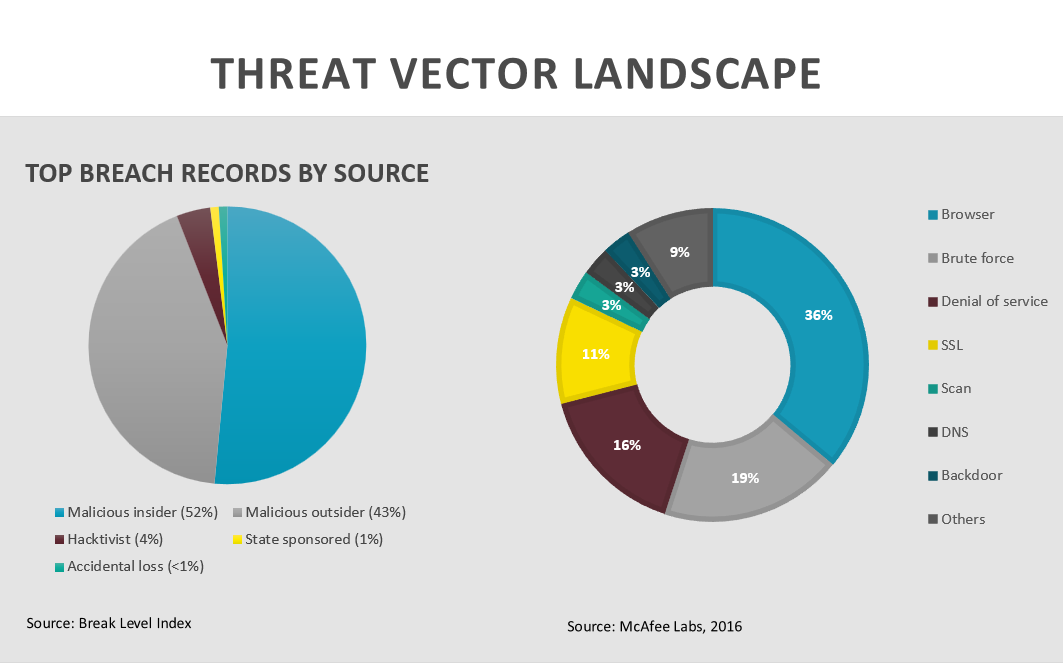
The graph on the left shows the percentage of internal versus external threats that an organization, like yours, can face, and the graph on the right shows the top seven types of attacks broken down by percentage.
As you can see from the graph on the left, it’s important to recognize that it’s not just outside threats you need to prepare for. Some attacks and data breaches, whether they’re intentional or accidental, can come from within your organization – a chilling thought.
The graph on the right shows that browser attacks (when a threat actor tries to trick internet surfers into downloading malware that is disguised as a software application or update) account for 36% of all attacks, with brute force attacks (when a threat actor attempts to decode a password or pin number through trial and error) coming in at 19%, and Denial of Service (DOS) attack, which prevents legitimate users from accessing services or information, accounting for 16% of all attacks out there.
Training your end users to be aware of these types of attacks can be a good way to ensure that you are protected from them. For more information on making your employees more cyber-aware, check out these two blogs:
|
Cybersecurity 101: Your End-Users are the First Line of Defense |
A Comprehensive Security Policy to Protect Your Organization from Cyberattacks |
Cyber Risk Management: Building a Culture of Security Practices & Principles
To build a strong corporate culture around privacy principles and leading security practices, there are some important questions that you need to ask yourself:
- Do you know who has access to your corporate data? Furthermore, can you guarantee that it’s only your employees who are accessing it?
- Do you know where your data is being stored at all times? Are you confident that any corporate data being accessed and stored on your employees’ devices is secure?
- Are you running annual security checks on your IT environment to flag any potential risks to your security posture?
- Do you know how your organization would respond to a potential breach?
- Do you have a well-documented security breach process, and, if so, are your employees well-versed in what to do in the event of a security breach?
- Do you talk about identity security with your staff or employees?
You need to consider all of these points - where your data’s being stored, who has access to it and when it’s being accessed, what potential risks are out there and how you’re going to be made aware of them, what happens if you are breached, and more – to be able to put together a solid cyber risk management policy for your organization.
Start Your Cyber Risk Management Journey with an Executive Cybersecurity Workshop
ProServeIT’s Executive Cybersecurity Workshop is a great way to start planning out your cyber risk management journey. In this workshop, ProServeIT’s security experts will go over the top cybersecurity concerns that your organization faces. We’ll help you to understand what risks you should be aware of, and how you can improve your security habits and behaviours. At the end of the workshop, we’ll also provide you with a custom security checklist that you can utilize in order to make sure that you’ve done what you need to in order to increase your overall security posture.
Want to Sign Up for An Executive Cybersecurity Workshop
Sign Me Up >>
Remember: Cyber Risk Management Isn’t Just for the Office
Of course, it’s important to also consider cyber risk management for your personal life, and at ProServeIT, we can also help you address this as well. What are some of your personal or family security concerns or risks? Do you take steps to reduce your security and privacy risks at home and in your personal life?
As part of our Executive Cybersecurity Workshop, we’ll talk about how you can answer these questions, and more. Like, for instance, do you know who your children are chatting with? Are you taking the same care to select personal passwords the way you select corporate ones? Have you had a conversation, as a family, on how you’re doing from a cybersecurity perspective?





