Turn your end users into cyber warriors with these top cybersecurity tips.
Another ransomware attack called GoldenEye, also known as NotPetya, has locked up devices worldwide since last Tuesday. Researchers have found that GoldenEye was designed to destroy data. If you were attacked by GoldenEye, despite the requested ransom payment, you would never see your stolen data again.
The traditional anti-virus software that many organizations are used to using is simply not enough for advanced threats like ransomware such as GoldenEye or WannaCry. To proactively protect your organization’s data from them, a holistic approach to security operations is strongly recommended.
A holistic security program takes into account security from an organization-wide viewpoint, incorporating not just IT but all aspects of the business. If you haven’t taken a holistic approach to your organization’s security, contact us to run a simple security assessment.
It will give you a complete picture of your security status. We will be able to assist you with building a customized plan from there.
One of the most important aspects of the holistic security and risk management program is an effective end-user training. Cyber criminals know that the weakest link in any organization’s security program is its end users.
This is why many advanced cyber attacks, such as ransomware and crypto malware, rely on human error to inflict damage.
Often, attacks start with a simple email message, disguised as a legitimate communication that just asks a user to click on a link. Once fooled, the user clicks the link and opens the door to whatever cyber attack has been planned.
This is exactly how the WannaCry and GoldenEye ransomwares gained access to thousands of networks worldwide.
End-user training is therefore crucial for any successful security programs. What is the most effective way to raise awareness and educate your end-users about the best security practices?
The answer is microlearning. Read on to learn what microlearning is and 5 tips to delivering effective end-user training. These will help you turn your end users into cyber warriors, proactively helping to defend your organization’s network and data.
What is Microlearning Method for End-User Security Education?
Microlearning is a learning methodology, consisting of short, engaging and highly effective training modules. This method allows organizations to reduce training fatigue and increase engagement.
Organizations have traditionally focused on annual training that addresses all security threats and best practices. It was meant to cause the least friction for end users and show compliance with training requirements.
However, as threats continue to evolve, this approach has become largely ineffective in ensuring that users are equipped with the current knowledge. The solution to this problem is microlearning.
Most organizations have security software in place to protect against external threats but end users can bypass some of these protocols unknowingly, in the due course of “just doing their job”. For example, they might shift from a corporate controlled device to a BYOD device because they were blocked on the controlled device but didn’t know why.
Sixty percent of all security incidents were recognized as originating with company-trusted individuals.
Many employees have access to system networks that in turn can access confidential and sensitive information. It is important to educate these users on the best practices needed for them to protect both themselves and the organization from any potential threats or attacks (Source: IBM Security Service 2016 Cyber Security Intelligence Index).
If you don’t have a current security awareness and training program, it is time to join the 68% of small-to-medium organizations that conduct cyber security training on an ongoing basis (Source: PwC 2015 Information Security Breaches Report).
5 Tips to Developing and Delivering an Effective Cyber Security Training

The key aspect of the microlearning method is that the end-user training delivers smaller portions of information on a more frequent basis.
This minimizes the effort to create an individual training session, reduces end-user training fatigue and makes the content more relevant to the end-users. Most importantly, end-users can get the most up-to-date information, which is important in the fast-changing cyber security landscape.
The goal is to teach your end users how to recognize current cyber attacks before they fall victim to them. Present the training as a personal and individualized issue so that your end-users will feel invested in their role as guardians of your network.
It is no longer just the organization that is affected by cyber security. The growing personal exposure to technology has increased individual risk, making the organization’s security training more relevant and important to end users.
Here are 5 tips to creating and delivering an effective end-user cyber security training program that will give your end-users important security knowledge they will retain and act upon:
- Tip 1. Make your security awareness training relatable to your users.
Focus your training program on the human element of cyber security so that users can understand the threats they are exposed to and know how to deal with them responsibly.
- Tip 2. Keep your training personal.
End users are more likely to give greater focus to cyber security training when it relates to their own personal lives. When discussing specific threats, give examples from both a business and personal point of view. Users are much more likely to relate if they know how a threat could target them on their own home computers as well as their office systems.
- Tip 3. Make end users self-aware.
Help your end users become more aware of the reasons behind why cyber criminals target them. This will help your users identify threats that may be trying to exploit them (such as clicking on unknown links in an email).
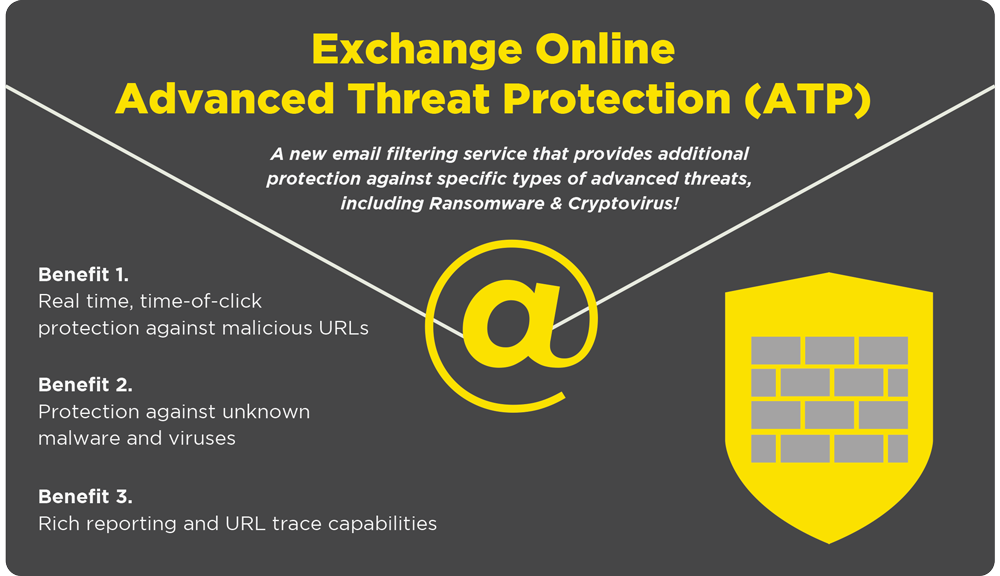
Office 365’s Advanced Threat Protection (ATP) is one of the useful tools that can help your end users be aware of the possible attacks they might face. ATP’s Safe Links feature proactively protects your users if they click such a link. ATP’s reporting and tracking capabilities provide you with critical insights into who is getting targeted in your organization. The price is only $2.40 CAD per user per month. Contact us if you’d like to find out more about ATP.
- Tip 4. Enlist your end users as malware sensors.
Proper training can go beyond just providing users with security knowledge; they can promote behavioural changes. Once your end-users begin to actively evaluate possible security risks, threat identification and risk mitigation will improve.
- Tip 5. Involve your end users as much as possible.
As with all holistic aspects of an effective security program, it is recommended that you involve your end users at all stages of training, from development to delivery. Consult all departments in your organization to solicit ideas for developing efficient training methods, facilitating the training and rolling it out. If done in a proper holistic manner, cyber security training will be owned by everyone in the organization and end-users will feel they have a direct stake in a successful outcome.
We Can Help You Create an Effective End User Security Training Program
Even the strongest Security and Risk Management Program is only as good as the people who are using your systems. Users can be tricked into giving unintended access to cyber criminals who, once inside your network, can bypass your carefully planned controls.
The key in mitigating this is to educate your end users about the potential threats, what to do if they encounter them, and instill in them the feeling that they have a major role to play in protecting their computing resources.
Don’t wait until your organization unwittingly becomes a victim of cyber crime. Whether you have formal user security training in place or not, we can help you create and implement a holistic cyber security training program that your end users will take to heart. Contact us today!